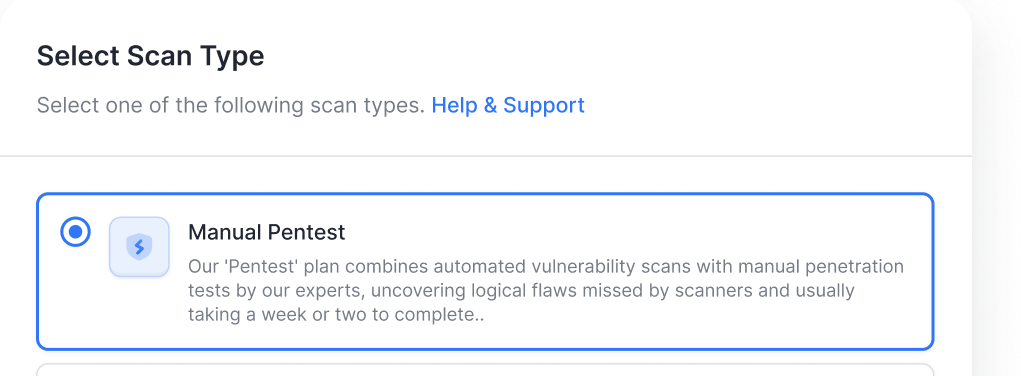
Move past the OWASP API Top 10 with API penetration testing that combines AI-powered scanning across 15,000+ test cases, in-house certified experts, and seamless CI/CD integration for continuous security
Better pricing, tailored to you. Book a call to unlock it

Last year alone, we at Astra Security:




Astra Security has been recognized by Gartner as a leading PTaaS vendor in the report “From Defense to Offense: How to Champion Proactive Cybersecurity
Trusted by 1000+ modern engineering teams





APIs power your business logic, carry sensitive data, and expose critical backend systems—yet most
lack comprehensive API security assessments between releases
Only 19% of security teams
feel their API security testing tools are effective
613 API endpoints
managed by organizations on an average, yet most lack complete visibility via robust API security assessment
5 out of 10
companies reported delays in product rollouts due to API security assessment issues
50% of ATO (approx)
(Account Takeover) attacks now target API endpoints
27% of attacks
exploit business logic—something API security scanning alone can’t catch
57% of companies
experienced at least one API-related breach in the last two years.
Only 19% of security teams
feel their API security testing tools are effective
613 API endpoints
managed by organizations on an average, yet most lack complete visibility via robust API security assessment
5 out of 10
companies reported delays in product rollouts due to API security assessment issues
50% of ATO (approx)
(Account Takeover) attacks now target API endpoints
27% of attacks
exploit business logic—something API security scanning alone can’t catch
57% of companies
experienced at least one API-related breach in the last two years.
Only 19% of security teams
feel their API security testing tools are effective
613 API endpoints
managed by organizations on an average, yet most lack complete visibility via robust API security assessment
5 out of 10
companies reported delays in product rollouts due to API security assessment issues
50% of ATO (approx)
(Account Takeover) attacks now target API endpoints
27% of attacks
exploit business logic—something API security scanning alone can’t catch
57% of companies
experienced at least one API-related breach in the last two years.
It’s time to rethink how we approach API security testing
Combine deep manual pentests with automated DAST to uncover critical risks scanners often miss.
15,000+ test cases for OWASP API Top 10, CVEs, and schema issues
Manual pentests for logic flaws like BOLA, IDOR, and broken auth
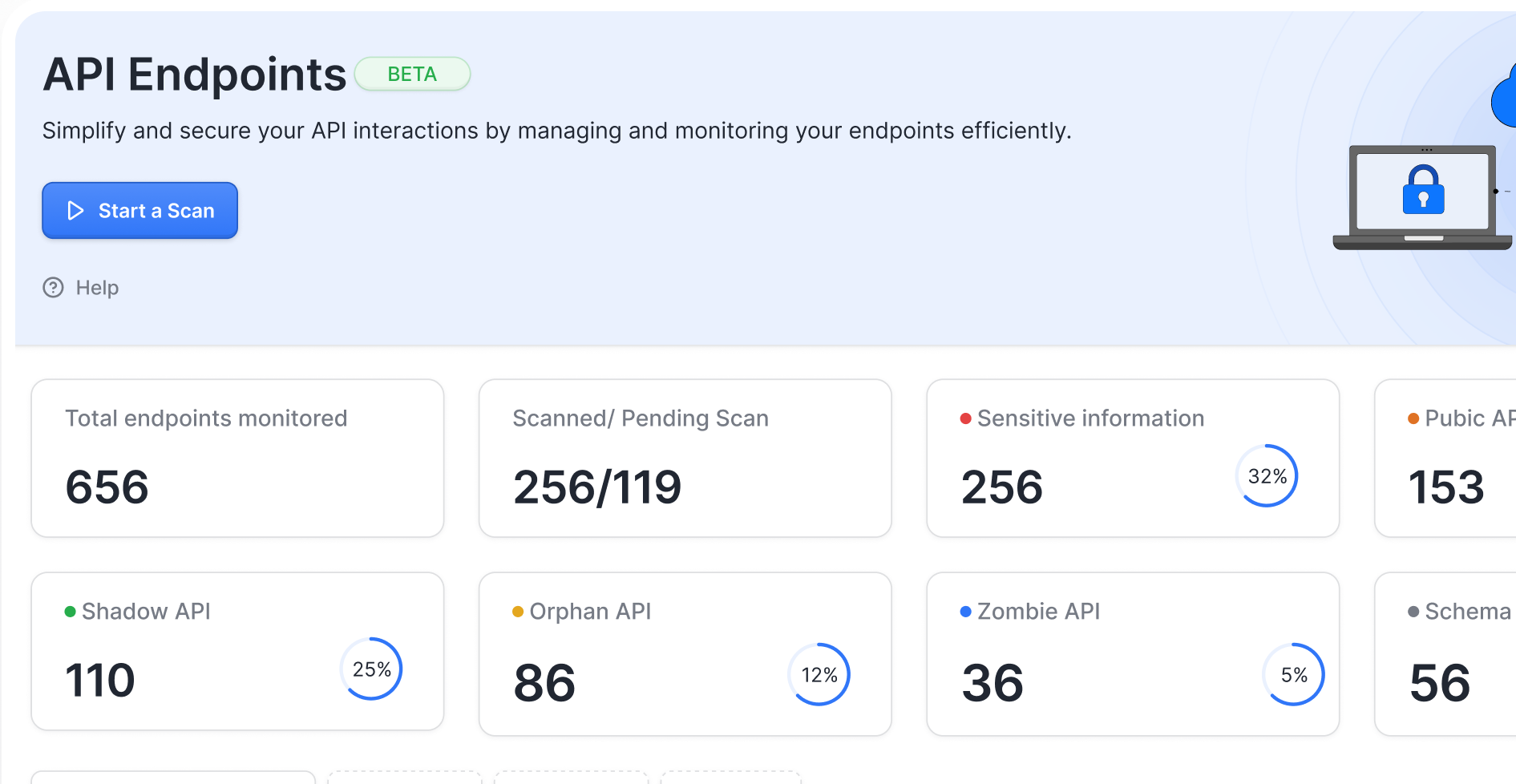
Find every API, including undocumented and shadow endpoints.
Captures live traffic from Postman, NGINX, Istio, AWS/GCP, and more
Builds a real-time API inventory with risk classification
Detects shadow/zombie APIs, undocumented endpoints, and usage anomalies
Security that integrates without slowing your builds or teams
Integrates with GitHub, GitLab, Jira, Slack, and CI/CD pipelines
Offers fix guidance in context
Dashboards built for both engineers and execs

Simulate real-world attack chains, not just signatures and patterns
Simulates logic-based attack chains
Flags missing validations, broken access controls, and PII exposure
Prioritizes high-risk endpoints like login, checkout, and reset flows

Secure APIs across any environment, fast
Supports REST, GraphQL, internal, and mobile APIs
Fits SaaS, cloud-native, and hybrid environments

OWASP TOP 10
BOLA, IDOR, Broken auth, mass assignment

Business logic flaws
Privilege escalation, insecure flows

Undocumented APIs
Detected through live traffic, not just OpenAPI specs

Misconfigurations
Schema violations, weak tokens, exposed keys

Data exposure risks
PII leaks, logging issues, and excessive data return

OWASP TOP 10
BOLA, IDOR, Broken auth, mass assignment

Business logic flaws
Privilege escalation, insecure flows

Undocumented APIs
Detected through live traffic, not just OpenAPI specs

Misconfigurations
Schema violations, weak tokens, exposed keys

Data exposure risks
PII leaks, logging issues, and excessive data return

OWASP TOP 10
BOLA, IDOR, Broken auth, mass assignment

Business logic flaws
Privilege escalation, insecure flows

Undocumented APIs
Detected through live traffic, not just OpenAPI specs

Misconfigurations
Schema violations, weak tokens, exposed keys

Data exposure risks
PII leaks, logging issues, and excessive data return
Dynamic vulnerability scanning designed to catch every risk.

Discover forgotten API endpoints your developers may have missed.

Run authenticated scans with a modern DAST scanner built for APIs.

Test against 15,000+ cases, including OWASP API Top 10, BOLA, and IDOR.

Capture live API traffic with connectors for AWS, GCP, Nginx, and Azure.

Integrate seamlessly with Postman and Burp Suite for continuous testing.

Identify real-world risks with AI-powered logic testing that extends beyond spec checks.

Detect shadow, zombie, and orphan APIs that never make it to documentation.

Identify PII leaks and secret disclosures happening through your APIs.
15,799 in 2024
$1,444
$19.6 million in 2024
> 44 days (industry avg: 60–150)
> 1 hour
Delivered DAST API scans & validated findings in under 1.5 days

Astra secures AI-first companies that handle billions of dollars in data, predictions, and decisions.












Astra Security meets global standards with accreditations from




CREST-approved member, CERT-In empaneled, PCI ASV-approved scanning vendor, and ISO 27001-certified







Offensive DAST vulnerability scanner that scans behind login for 10,000+ test cases like OWASP Top 10, ports, CVEs & more


Simply put, a domain with all its site tree URLs is a target. Target can be the URL of a web application, IP, website, API etc.
If your website makes API calls to different domains (eg: api.example.com), you can add them as an extra host during setup without having to purchase another target for it, and all calls to api.examples.com from example.com will be scanned.


Simply put, a domain with all its site tree URLs is a target. Target can be the URL of a web application, IP, website, API etc.
If your website makes API calls to different domains (eg: api.example.com), you can add them as an extra host during setup without having to purchase another target for it, and all calls to api.examples.com from example.com will be scanned.


Simply put, a domain with all its site tree URLs is a target. Target can be the URL of a web application, IP, website, API etc.
If your website makes API calls to different domains (eg: api.example.com), you can add them as an extra host during setup without having to purchase another target for it, and all calls to api.examples.com from example.com will be scanned.


Simply put, a domain with all its site tree URLs is a target. Target can be the URL of a web application, IP, website, API etc.
If your website makes API calls to different domains (eg: api.example.com), you can add them as an extra host during setup without having to purchase another target for it, and all calls to api.examples.com from example.com will be scanned.
Hacker style pentest by certified pentesters made agile & dev friendly with PTaaS platform. Meet & exceed SOC2, ISO, HIPAA needs

Unlimited vulnerability scans with 3000+ tests (OWASP, SANS etc.)

Unlimited integrations with CI/CD tools, Slack, Jira & more

Four expert vetted scan results to ensure zero false positives when billed yearly

Compliance reporting for SOC2, ISO27001, PCI-DSS, HIPAA etc.

Everything in the Scanner plan






Weekly vulnerability scans with 3000+ tests (OWASP, SANS etc.)

Essential features like pentest dashboard, PDF reports and scan behind login
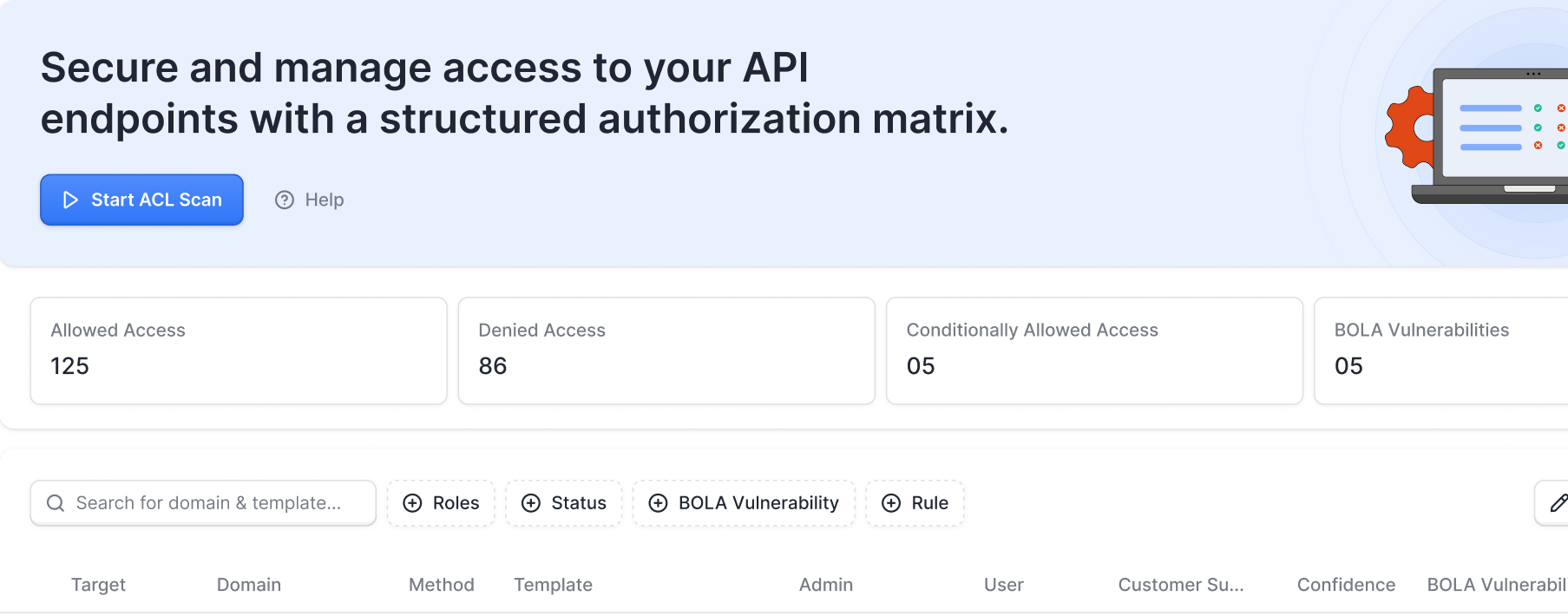
Continuously discover & scan every API in your infrastructure for broken access control, authorization flaws, OWASP Top 10 & more


Our customers rely on Astra’s continuous pen testing to keep their applications secure, compliant, and breach-proof.

We are impressed by Astra's commitment to continuous rather than sporadic testing.



Astra not only uncovers vulnerabilities proactively but has helped us move from DevOps to DevSecOps



Their website was user-friendly & their continuous vulnerability scans were a pivotal factor in our choice to partner with them.



The combination of pentesting for SOC 2 & automated scanning that integrates into our CI pipelines is a game-changer.



I like the autonomy of running and re-running tests after fixes. Astra ensures we never deploy vulnerabilities to production.



We are impressed with Astra's dashboard and its amazing ‘automated and scheduled‘ scanning capabilities. Integrating these scans into our CI/CD pipeline was a breeze and saved us a lot of time.



We are impressed by Astra's commitment to continuous rather than sporadic testing.



Astra not only uncovers vulnerabilities proactively but has helped us move from DevOps to DevSecOps



Their website was user-friendly & their continuous vulnerability scans were a pivotal factor in our choice to partner with them.



The combination of pentesting for SOC 2 & automated scanning that integrates into our CI pipelines is a game-changer.



I like the autonomy of running and re-running tests after fixes. Astra ensures we never deploy vulnerabilities to production.



We are impressed with Astra's dashboard and its amazing ‘automated and scheduled‘ scanning capabilities. Integrating these scans into our CI/CD pipeline was a breeze and saved us a lot of time.

