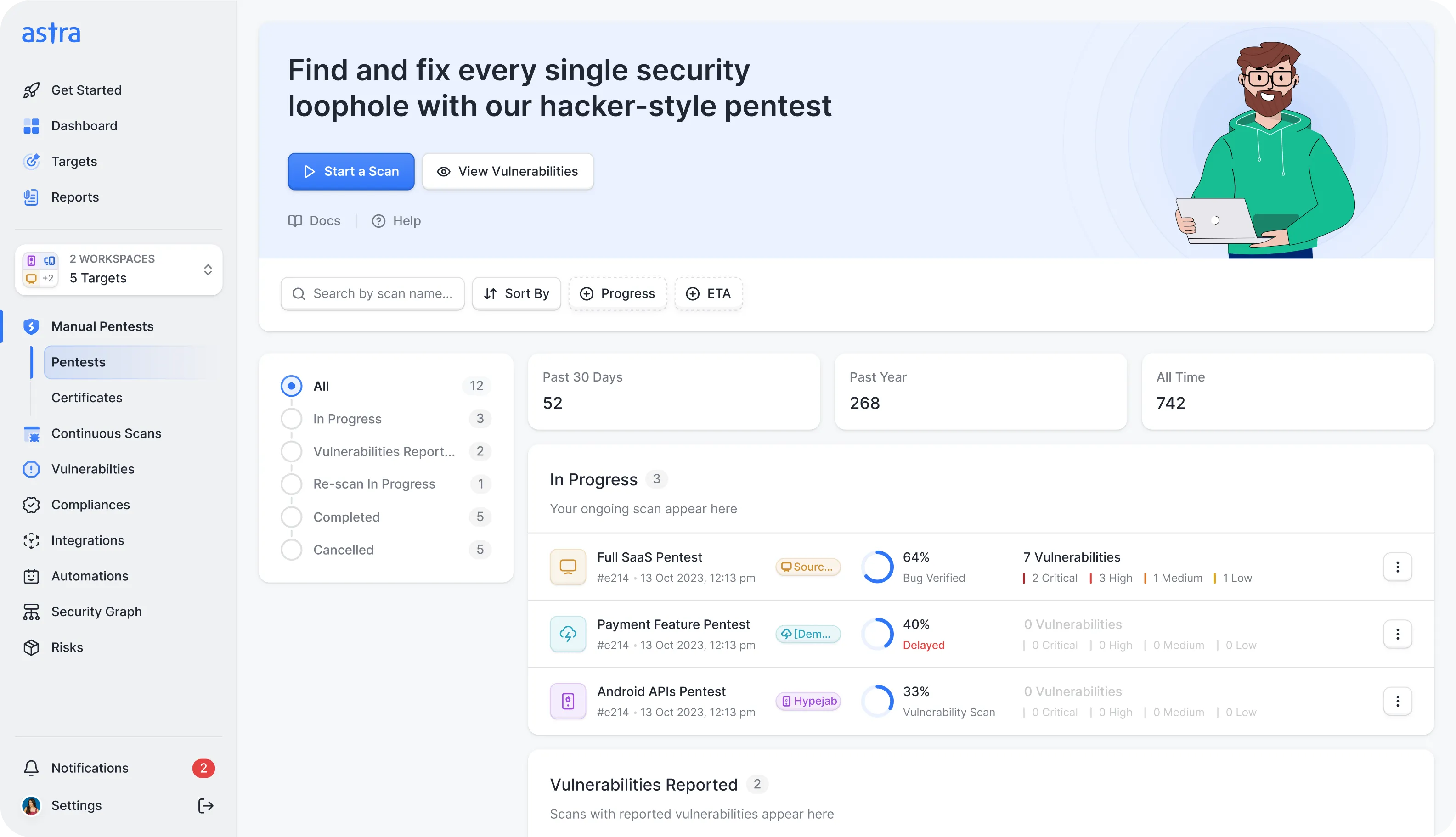
Find and fix every single vulnerability in your web app with Astra Pentest
We simulate real-world attacks to uncover vulnerabilities, test authentication & business logic flaws,
and provide remediation steps with our web application penetration testing services.
3000+
Pentests Done
21 Million +
Vulnerabilities Uncovered
4.6/5
On G2.com
Astra’s one of a kind Web Pentest Platform
turns your web app into fort knox
Setup & Onboarding
Go from sign-up to discovering vulnerabilities in minutes. Our self-serve onboarding accelerates web application penetration testing while giving you support from your CSM whenever needed.

Manual Penetration Test
Identify threats and attack vectors with comprehensive manual and automated web app pentesting in 8-15 business days. Scrutinize emerging CVEs, business logic flaws, and authentication weaknesses for complete application security testing.

Reporting & Remediation
Improve your security posture with actionable reports, video PoCs and detailed steps to fix a vulnerability. Get two re-scans to validate fixes and Astra's publicly verifiable certificate once you pass the pentest.

Pentest Certificate
Show off your security chops! Once we've validated your fixes, you'll receive Astra's publicly verifiable pentest certificate. It's like a security badge of honor for your web app.

Continuous Pentesting
The security party doesn't stop! Keep your app safe 24/7 with our DAST scanner and API security platform. Plus, use our PTaaS capabilities to continuously pentest every shiny new feature you build. Because in the world of web apps, security never sleeps.

Our web app pentesters? World class, certified & contributors to top security projects
We find the bugs before the bad guys do
Our team stays ahead of the curve in the ever-evolving world of web security

.avif)
.avif)
.avif)

Ever evolving test case library &
AI powered threat modeling

Makes our pentesters 2x more effective in uncovering vulnerabilities in web applications
Ensures consistent, high-quality testing regardless of human factors
Generates tailored test cases for your specific application
Helps you understand & fix vulnerabilities quicker with full context of your application
Think the pentest is the end?
It's just the beginning.
We don't leave you high and dry post the pentest.
With Astra, a successful web app pentest is
the start of your security journey.
Regular automated scans with our DAST scanner having 10,000+ test case library

API security scanning that never sleeps

Continuous pentesting for your shiny new features
We play nice with your tools: GitHub, GitLab, Slack, JIRA - you name it
The wrong web application pentesting could
cost you big time
Lack support from experienced Security Experts
Are not comprehensive enough & often miss out issues
Don’t provide step-by-step guidance on fixing issues
Don’t help you prioritize and make the right fixes
Lack collaborative vulnerability management dashboard
Make it hard to test new features or product versions
Lack support from experienced Security Experts
Are not comprehensive enough & often miss out issues
Don’t provide step-by-step guidance on fixing issues
Don’t help you prioritize and make the right fixes
Lack collaborative vulnerability management dashboard
Make it hard to test new features or product versions
Lack support from experienced Security Experts
Are not comprehensive enough & often miss out issues
Don’t provide step-by-step guidance on fixing issues
Don’t help you prioritize and make the right fixes
Lack collaborative vulnerability management dashboard
Make it hard to test new features or product versions
Lack support from experienced Security Experts
Are not comprehensive enough & often miss out issues
Don’t provide step-by-step guidance on fixing issues
Don’t help you prioritize and make the right fixes
Lack collaborative vulnerability management dashboard
Make it hard to test new features or product versions
Lack support from experienced Security Experts
Are not comprehensive enough & often miss out issues
Don’t provide step-by-step guidance on fixing issues
Don’t help you prioritize and make the right fixes
Lack collaborative vulnerability management dashboard
Make it hard to test new features or product versions
Lack support from experienced Security Experts
Are not comprehensive enough & often miss out issues
Don’t provide step-by-step guidance on fixing issues
Don’t help you prioritize and make the right fixes
Lack collaborative vulnerability management dashboard
Make it hard to test new features or product versions
Modern web apps are intricate. Our expertise? Unmatched.
We understand the complexity of today's web applications. Our comprehensive offensive pentest approach dissects web apps into layers, and tests every layer:
API-first architectures
Microservices
Complex cloud infrastructures
And every layer in between
From startups to Fortune companies, 1000+ companies trust Astra


.avif)





































.webp)









Frequently asked questions
What is included in Astra’s Web App Pentesting Services?
How long does a typical web application penetration test take?
What types of vulnerabilities are identified during a web application pentest?
How does the pricing work?
I have a specific scope, can you tailor the pricing?

Ready to secure your complex web app?