Continuous automated pentesting with 15,000+ real-world test cases, behind-login coverage, and CVE checks—validated by experts to deliver actionable, noise-free reports that save dev hours.
Better pricing, tailored to you. Book a call to unlock it

Last year alone, we at Astra Security:




Trusted by 1000+ modern engineering teams






Lightning Scan
A fast, high-level scan designed to identify common vulnerabilities quickly

Emerging threat scan
A scan focused on identifying vulnerabilities associated with newly discovered threats

Full scan
An in-depth scan that thoroughly examines the target for a broad range of vulnerabilities

Delta scan
An incremental scan that focuses only on the parts of your application that have changed

Automated Crawling (Web)
Builds and updates inventory without scanning, with scheduled or on-demand crawls


Server-Side Request Forgery
Tricks the server into making unintended requests, potentially exposing internal systems

SQL Injection
Injects malicious queries into databases to read, modify, or delete sensitive data

Secret Leaking
Exposes credentials, API keys, or tokens that attackers can exploit for unauthorized access

Cross-Site Scripting
Injects malicious scripts into web pages, targeting users to steal data or hijack sessions

Server-Side Request Forgery
Tricks the server into making unintended requests, potentially exposing internal systems

SQL Injection
Injects malicious queries into databases to read, modify, or delete sensitive data

Secret Leaking
Exposes credentials, API keys, or tokens that attackers can exploit for unauthorized access

Cross-Site Scripting
Injects malicious scripts into web pages, targeting users to steal data or hijack sessions

Server-Side Request Forgery
Tricks the server into making unintended requests, potentially exposing internal systems

SQL Injection
Injects malicious queries into databases to read, modify, or delete sensitive data

Secret Leaking
Exposes credentials, API keys, or tokens that attackers can exploit for unauthorized access

Cross-Site Scripting
Injects malicious scripts into web pages, targeting users to steal data or hijack sessions
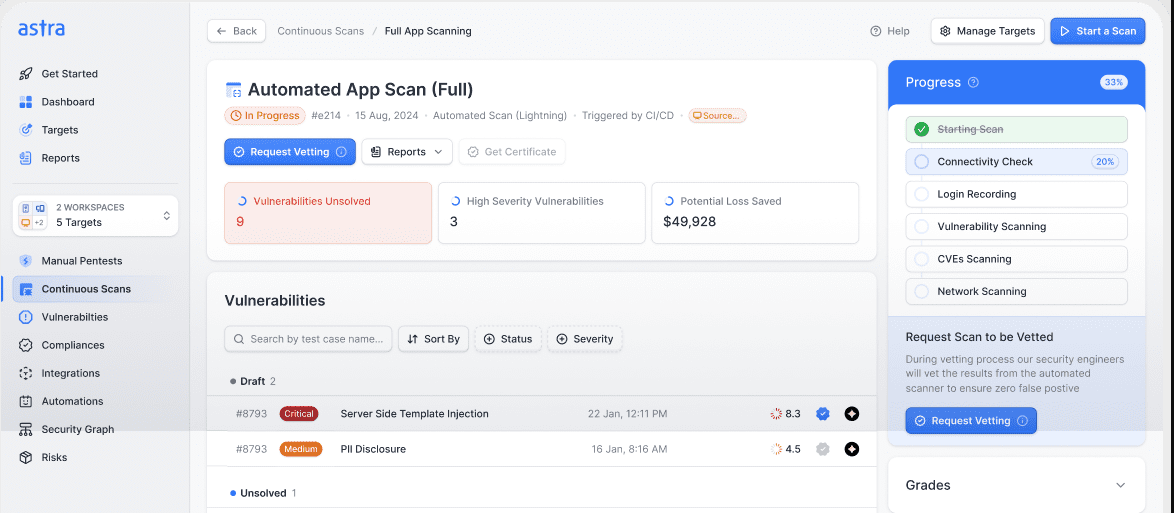
Scan each new feature incrementally, ensuring continuous security without slowing down
your development cycle. Our penetration testing as a service (PTaaS) platform integrates
seamlessly with your workflow, allowing you to maintain rapid feature deployment
while enhancing your security posture.
Astra’s pen testing methodology blends automated scans with manual techniques,
enabling you to remediate real-world vulnerabilities faster.

Zombie API
Old, forgotten APIs left running, creating unmonitored security risks

Shadow API
Undocumented or unknown APIs outside official oversight, exposing blind spots

Orphan API
APIs no longer tied to an application but still active, vulnerable to exploitation

PII Exposure
Leaks personally identifiable information, risking compliance violations and identity theft

BOLA/IDOR
Lets attackers manipulate object IDs to gain unauthorized access to data or functions

Zombie API
Old, forgotten APIs left running, creating unmonitored security risks

Shadow API
Undocumented or unknown APIs outside official oversight, exposing blind spots

Orphan API
APIs no longer tied to an application but still active, vulnerable to exploitation

PII Exposure
Leaks personally identifiable information, risking compliance violations and identity theft

BOLA/IDOR
Lets attackers manipulate object IDs to gain unauthorized access to data or functions

Zombie API
Old, forgotten APIs left running, creating unmonitored security risks

Shadow API
Undocumented or unknown APIs outside official oversight, exposing blind spots

Orphan API
APIs no longer tied to an application but still active, vulnerable to exploitation

PII Exposure
Leaks personally identifiable information, risking compliance violations and identity theft

BOLA/IDOR
Lets attackers manipulate object IDs to gain unauthorized access to data or functions
Scan each new feature incrementally, ensuring continuous security without slowing down
your development cycle. Our penetration testing as a service (PTaaS) platform integrates
seamlessly with your workflow, allowing you to maintain rapid feature deployment
while enhancing your security posture.
Astra’s pen testing methodology blends automated scans with manual techniques,
enabling you to remediate real-world vulnerabilities faster.
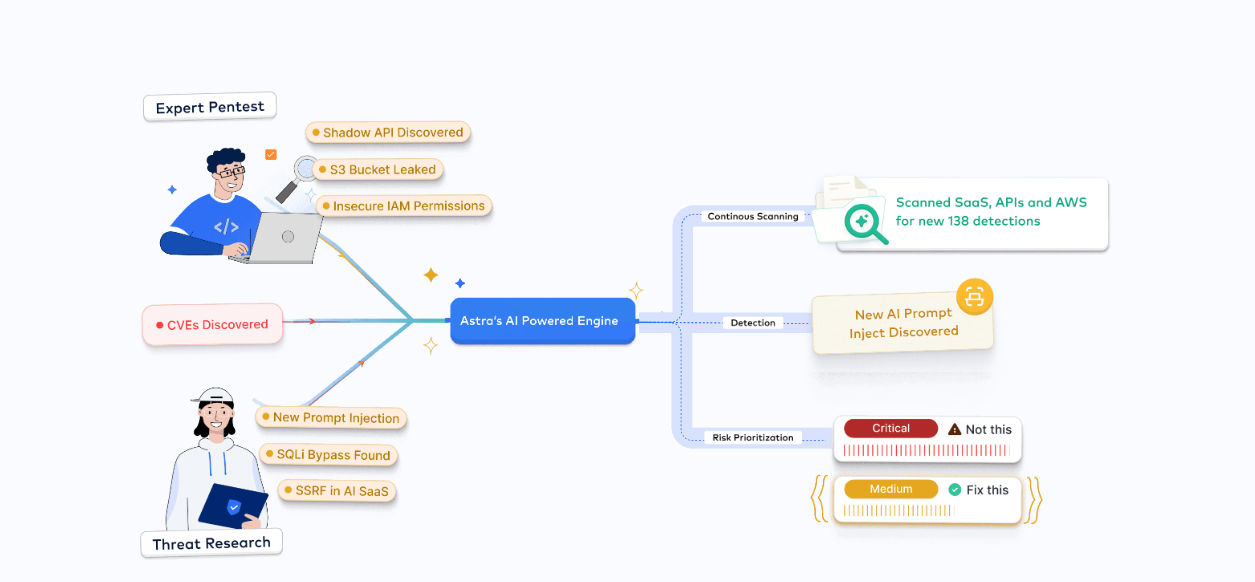
Every pentest our security engineers perform feeds back into our DAST vulnerability scanner.
That means we're not just relying on known CVEs - we're continuously learning
from real-world hacks performed during pentests.


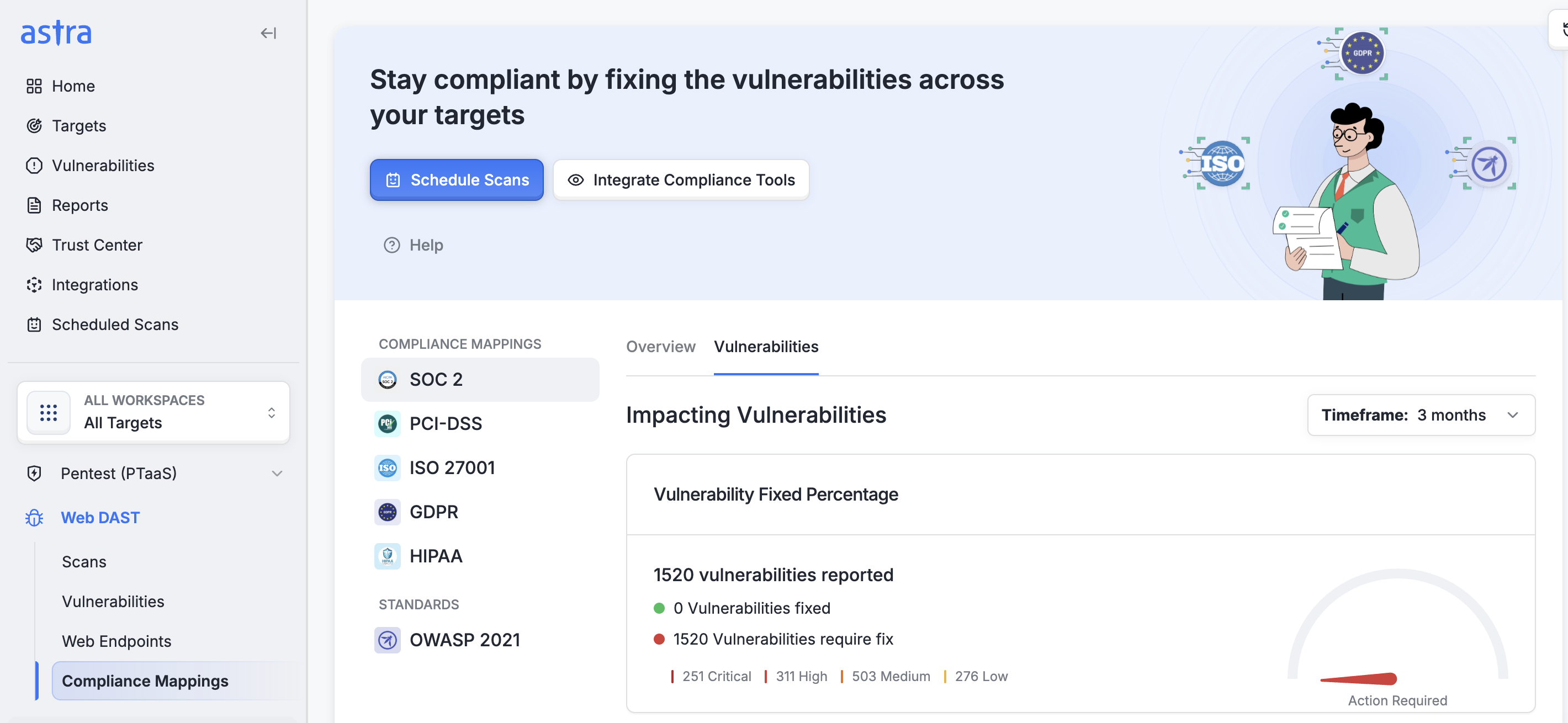
Astra meets global standards with accreditations from




We find the bugs before the bad guys do
Our team stays ahead of the curve in the ever-evolving world of web security

.avif)
.avif)
.avif)

Our customers rely on Astra’s continuous pen testing to keep their applications secure, compliant, and breach-proof.

We are impressed by Astra's commitment to continuous rather than sporadic testing.



Astra not only uncovers vulnerabilities proactively but has helped us move from DevOps to DevSecOps



Their website was user-friendly & their continuous vulnerability scans were a pivotal factor in our choice to partner with them.



The combination of pentesting for SOC 2 & automated scanning that integrates into our CI pipelines is a game-changer.



I like the autonomy of running and re-running tests after fixes. Astra ensures we never deploy vulnerabilities to production.



We are impressed with Astra's dashboard and its amazing ‘automated and scheduled‘ scanning capabilities. Integrating these scans into our CI/CD pipeline was a breeze and saved us a lot of time.



We are impressed by Astra's commitment to continuous rather than sporadic testing.



Astra not only uncovers vulnerabilities proactively but has helped us move from DevOps to DevSecOps



Their website was user-friendly & their continuous vulnerability scans were a pivotal factor in our choice to partner with them.



The combination of pentesting for SOC 2 & automated scanning that integrates into our CI pipelines is a game-changer.



I like the autonomy of running and re-running tests after fixes. Astra ensures we never deploy vulnerabilities to production.



We are impressed with Astra's dashboard and its amazing ‘automated and scheduled‘ scanning capabilities. Integrating these scans into our CI/CD pipeline was a breeze and saved us a lot of time.

