Azure Penetration Testing Services
Expert-led Azure pentesting services + continuous monitoring, mapped to CSA Cloud Controls Matrix (CCM) and CIS Benchmarks. alongside CVSS v4.0 reporting with ISO 27001, SOC2, GDPR, and HIPAA compliance readiness. Seamless Jira, Slack, and CI/CD integration.











- 400+ exploit-informed rules built for AWS, Azure, and GCP.
- Real-time validation cuts false positives by up to 90%.
- Credential-aware scans replicate real attacker access paths.
- Publicly verifiable certifications with shareable links.
- Demonstrate your security commitment.
- Build client and partner trust.
- Summarize your security posture for easy sharing with customers and auditors
- Integrate into CI/CD with GitHub Actions, GitLab CI, Jenkins, Bitbucket, and more.
- Automate scans, send vulnerability alerts via Slack
- Create JIRA tickets, all without leaving your pipeline.
- Continuous scans and pentests for AWS, Azure, and GCP, no setup needed
- Full visibility into IAM, storage, workloads, and perimeter across regions
- Expert-tuned accuracy with vulnerabilities triaged by business impact
- Compliance-ready reports with step-by-step fixes and instant rescans
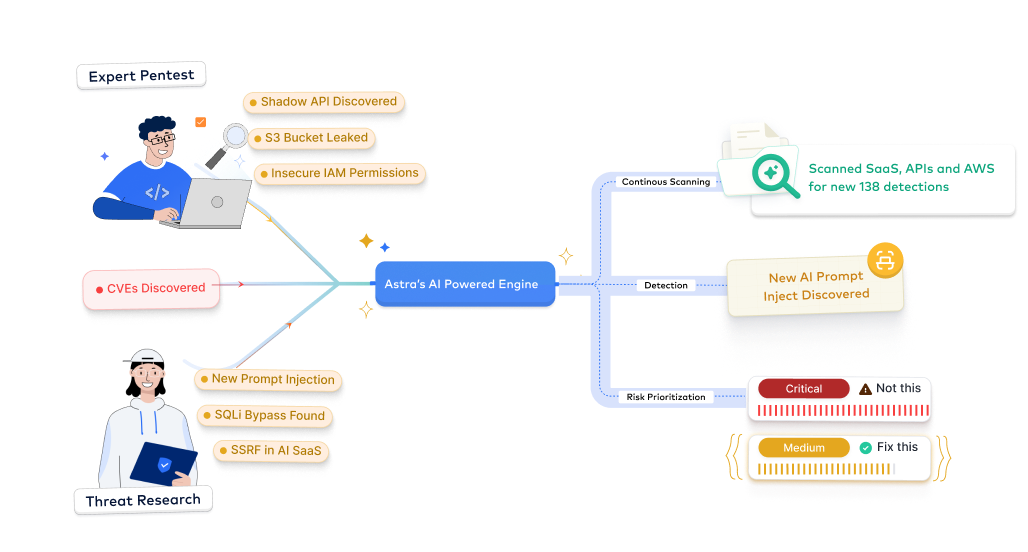
- ML models trained on 3,000+ real-world exploit patterns.
- Context-aware remediation mapped directly to developer workflows
- Adaptive detection logic identifies drift and insecure defaults with 40% higher accuracy.

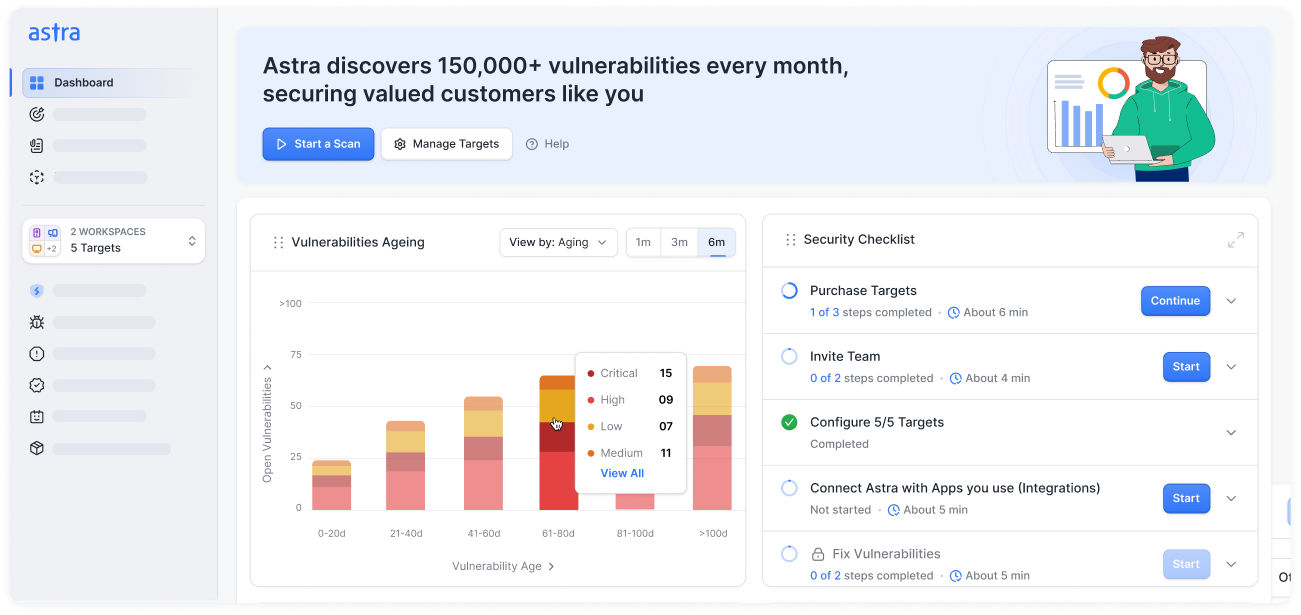
Astra's 7-Step Pentest Process
How our Azure penetration testing works
Astra's hacker-style pentest process combines years of pentester experience, cutting-edge AI, and deep knowledge of industry standards. Our battle-tested approach ensures comprehensive coverage, uncovering vulnerabilities that others miss.
Discovery & Access


Config Posture Review
Manual Validation & Exploitation


Reporting & Handoff
Rescan & Attestation


From startups to fortune companies,
1000+ companies trust Astra












































.webp)





Types of vulnerabilities we detect
Our Azure penetration testing services provide full coverage, targeting vulnerabilities wherever they emerge

Identity & Access

Storage & Data

Network & Perimeter

Workloads

Logging & Monitoring
Compliance Gaps





Experience the Astra Security difference: faster, smarter, compliance-ready pentesting.
Pentesting as a service, tailored for your industry
Continuous penetration testing and compliance mapping services built for ISO, SOC 2, HIPAA, PCI DSS, and more.

- Secure financial systems and payment workflows from logic flaws
- Deliver actionable fixes and maintain PCI DSS, ISO 27001, SOC 2, DORA compliance, and more
- Standards: OWASP, PTES, CVSS

- Protect patient data and secure APIs across web, mobile, and cloud
- Uncover hidden PHI exposures and validate HIPAA, ABHA, and more
- Standards: OWASP, PTES, NIST, CVSS

- Accelerate app security with DevSecOps integration and continuous scans
- Detect vulnerabilities with AI-driven validation and ensure ISO 27001, SOC 2, GDPR compliance and more
- Standards: OWASP, PTES, CVSS, NIST SP 800-115

- Protect customer data and secure payment flows from BOLA/IDOR risks
- Empower developers with guided remediation and PCI DSS, ISO 27001, SOC 2 compliance and more
- Standards: OWASP, PTES, CVSS

- Fortify cloud, container, and on-prem systems with authenticated tests
- Monitor and validate vulnerabilities to prevent downtime; comply with NIST, ISO 27001, SOC 2, CREST, Cert-In, and more
- Standards: OWASP, PTES, NIST, CVSS

- Discover shadow APIs and secure cloud services
- Deliver fast, developer-friendly fixes; ensure GDPR, ISO 27001, SOC 2 compliance
- Standards: OWASP, PTES, CVSS
Our pentesters? World class, certified & contributors to top security projects
We find the bugs before the bad guys do
Our team stays ahead of the curve in the ever-evolving world of web security

.avif)
.avif)
.avif)





Stay compliant throughout the year
Understand our industry-specific pentests as a service plans designed to meet your compliance, scale, and security needs.
- Get compliance-ready year-round for ISO 27001, SOC 2, GDPR, HIPAA, PCI DSS, CREST, CERT-In, CIS Controls, NIST, & more
- Receive actionable insights from continuous pentesting and expert-led remediation guidance
- Track compliance progress with the Astra Security Compliance View, providing executive-friendly and technical views


- Maintain audit-ready reports without manual effort
- Reduce risk exposure with real-time detection and validation
- Prioritize remediation based on business impact and compliance requirements
- Demonstrate security maturity to clients, regulators, and internal stakeholders


Frequently asked questions
What is Azure penetration testing, and why is it important?
Azure penetration testing evaluates the security of applications, workloads, and configurations hosted on Microsoft Azure. It identifies vulnerabilities specific to cloud environments, helping organizations reduce risk, prevent breaches, and maintain compliance while ensuring resilient performance of critical business systems.
How is Azure penetration testing different from regular pentesting?
Unlike traditional pentesting, Azure penetration testing focuses on Azure-specific services such as Active Directory, storage accounts, virtual networks, and role-based access controls. It considers Microsoft’s shared responsibility model and unique cloud configurations that may not exist in on-premises or hybrid environments.
What types of vulnerabilities can Azure penetration testing uncover?
Testing can uncover misconfigured role assignments, insecure APIs, exposed storage accounts, weak authentication, excessive permissions, unpatched virtual machines, flawed firewall rules, and identity-based attacks. It also detects risks in hybrid or multi-cloud integrations where Azure resources interact with external systems.
What is included in your Azure penetration testing service?
The service typically includes scoping of Azure assets, assessment of IAM, storage, and networking configurations, simulated attack scenarios, exploitation of discovered weaknesses, and a detailed report with remediation guidance. Both executive and technical reports map findings to compliance requirements and business impact.
How often should I perform Azure penetration testing?
Azure environments should be tested at least annually, with additional tests after major deployments, new application launches, or significant configuration changes. High-risk industries or businesses with sensitive data may require quarterly or continuous testing to maintain strong cloud security.
How long does Azure penetration testing take?
The duration depends on scope and complexity. Smaller, targeted tests may take a few days, while large-scale Azure environments with multiple applications and integrations may require two to four weeks. Timelines also include reporting and remediation consultation after testing.











