#1 Continuous Vulnerability Scanning Services (Trusted by 1000+ Teams)
Detect and validate vulnerabilities across web, API, and cloud layers with automated continuous vulnerability scanning services. Our team pairs tuned automation with expert review to remove false positives, map findings to compliance, and hand engineers prioritized, SLA-backed remediation steps.

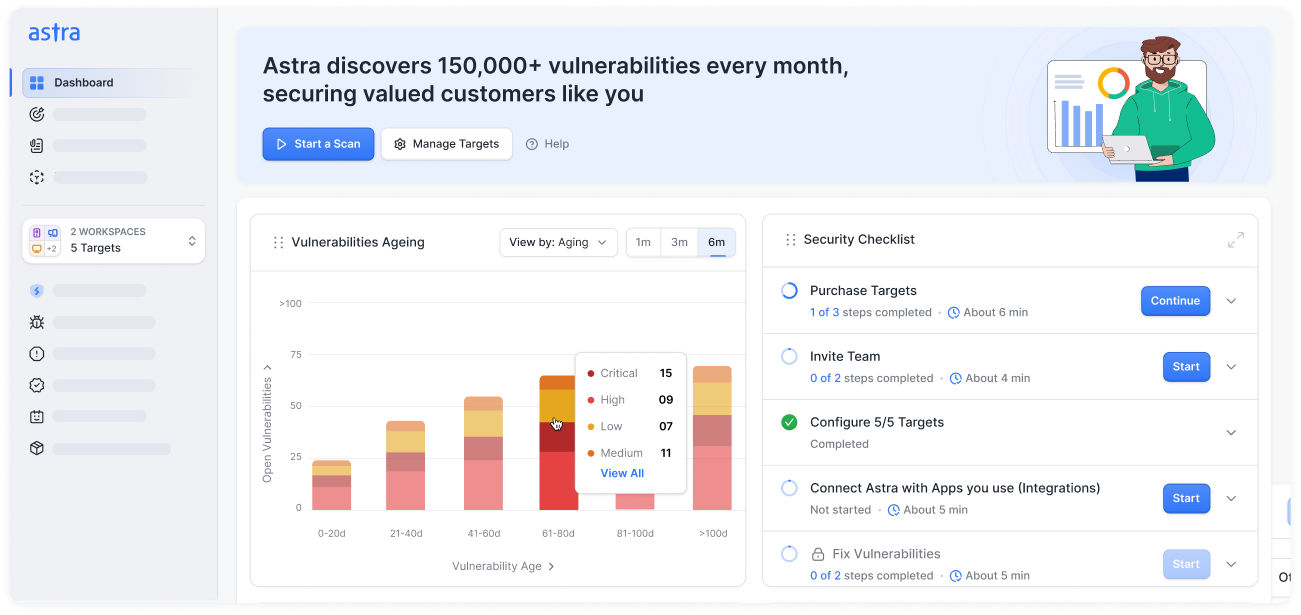










Why choose Astra Security's continuous vulnerability scanning services?
Experience our DAST, API, and cloud scanner plans built for modern security teams with expert-driven testing, smart automation, and continuous protection at scale.
- Focus on real vulnerabilities with noise-free detection logic
- Our experts vet false positives so you don’t waste hours validating noise
- Mark verified issues once to skip them in future scans
- Get expert vulnerability reviews for faster prioritization
- Cut manual tuning as our AI-first vulnerability scanner adapts tests to your app
- Context-aware analysis improves accuracy & guidance with every scan
- Use machine learning models that evolve from real-world exploit data
- Scale testing without increasing security headcount
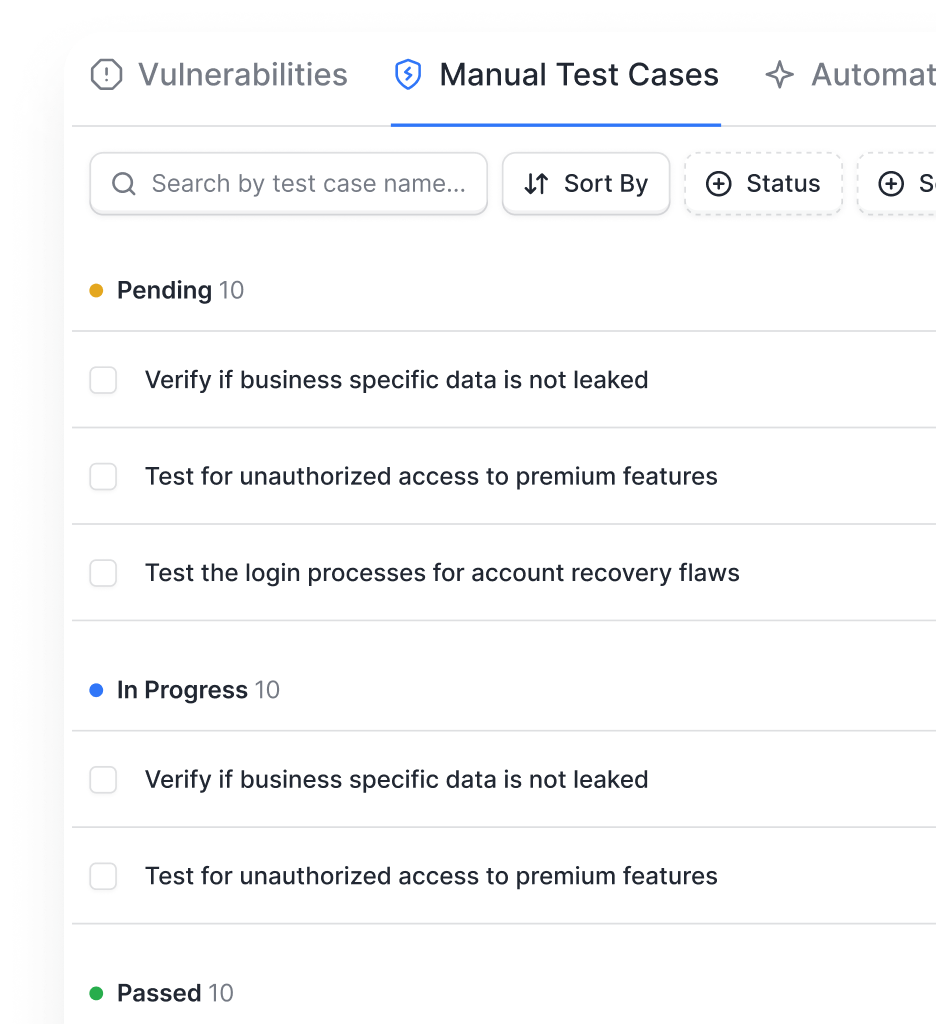
- Get continuous vulnerability scans and protection across web, API, and cloud
- Avoid alert fatigue with business-impact optimized vulnerabilities & expert-tuned DAST scans
- Stay compliant with automated reports, verified fixes, and targeted automated rescans
- Cut false positives and reduce total cost with managed accuracy of vetted scans
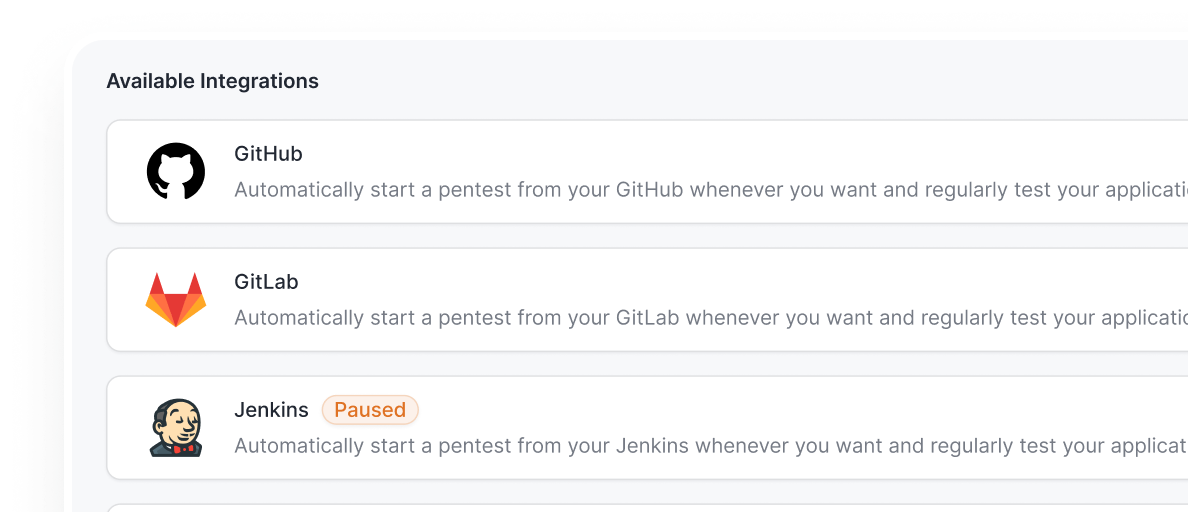
- Integrate testing seamlessly into your CI/CD workflows (GitHub, GitLab, CI, Jenkins, Bitbucket, & more) with zero release delays
- Automate scans, Slack vulnerability alerts, and JIRA ticketing to cut manual work
- Shorten your mean time to remediate with seamless vulnerability workflows
- Maintain speed-to-market without compromising security
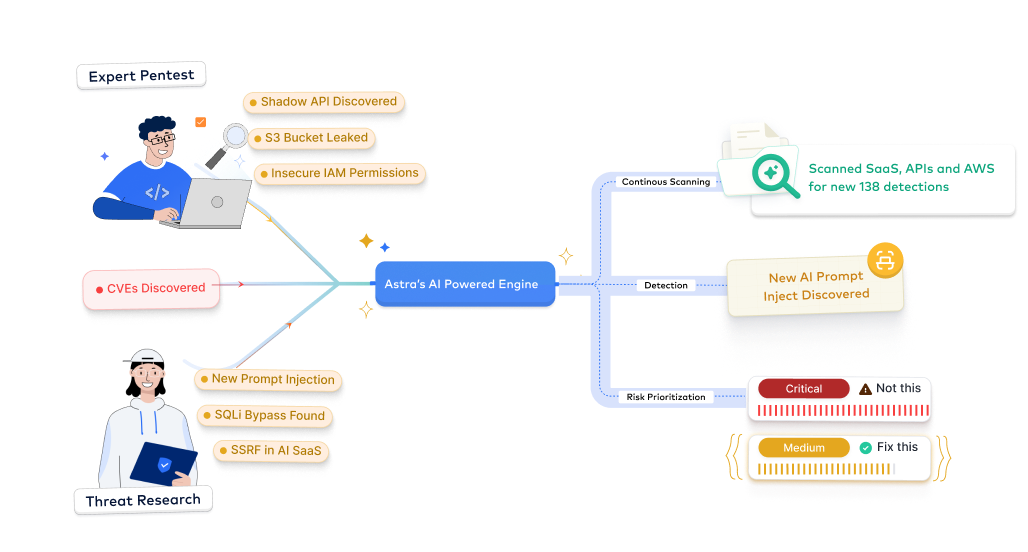
- Generate detailed scan reports with vulnerabilities mapped to ISO, PCI, SOC 2, HIPAA, GDPR, OWASP, NIST, and other standards
- Demonstrate security maturity to shorten sales cycles
- Turn compliance readiness into a sales advantage

Simulate real-world attacks, uncover hidden risks, and strengthen your defenses with expert-led continuous vulnerability scanning services for just $69.
Start TrialAstra's 7-Step Pentest Process
How our black box testing works
Astra’s 6-step black box methodology starts with zero context, probing your system just like a malicious actor would, to reveal how exploitable your assets really are.
Discovery & Scoping
- Identify all in-scope applications, APIs, domains, and subdomains for testing
- Define parameters, environments, and integrations to ensure complete coverage
- Align the assessment scope with relevant compliance frameworks such as PCI DSS, ISO 27001, SOC 2, or HIPAA
- Personalized setup to maintain visibility throughout the engagement
Outcome: Outline a mutually-agreed compliance-guaranteed scope and a clear roadmap to audit readiness


Authentication Setup
- Establish secure authentication workflows for behind-login testing across user roles, APIs, and SSO flows
- Integrate credentials, tokens, and session configurations to enable deep authenticated coverage
- Ensure safe testing within staging or production replicas without disrupting business operations
- Standardized authentication templates for future scans to streamline recurring assessments
Outcome: Get full-depth testing coverage without risking business downtime or continuity
Automated Baseline
- Run automated continuous vulnerability scans across web, API, & cloud layers to detect OWASP Top 10, CVEs, business logic flaws, and misconfigs
- Leverage Astra Security’s tuned detection engine for comprehensive baseline coverage and minimized false positives
- Correlate automated findings with prior assessments to maintain historical visibility
- Deliver continuous monitoring data supporting ongoing compliance & audit preparation
Outcome: Gain a comprehensive, continuous threat baseline ready for immediate action and audit reporting


Risk Scoring
- Evaluate each finding based on impact, business impact, and compliance relevance
- Apply contextual CVSS scoring to prioritize remediation according to organizational risk appetite
- Highlight vulnerabilities that may delay certifications or create regulatory exposure
- Generate clear risk summaries to guide both technical and executive decision-making
Outcome: Receive prioritized, actionable risk intelligence focused on business & regulatory exposure
Remediation Support
- Deliver detailed, developer-focused remediation steps validated by our expert pentesters
- Provide reproducible PoCs, payloads, and configuration guidance for faster fixes
- Get documented remediation evidence aligned with audit & compliance requirements
Outcome: Achieve faster, verified fixes supported by our team and documented for full compliance


Re-Scan & Validate
- Conduct targeted re-tests to confirm successful remediation and eliminate residual risks
- Schedule recurring scans to detect regressions after updates or infrastructure changes
- Capture time-stamped validation evidence for audit readiness and certification renewals
- Maintain a verified security baseline that demonstrates continuous improvement over time
Outcome: Maintain audit-ready proof that confirms fixes, prevents regressions, and demonstrates continuous security maturity.
From startups to fortune companies,
1000+ companies trust Astra












































.webp)





Experience zero false positives and seamless integrations with Astra Security’s continuous vulnerability management service.
Request Security ServicesTypes of continuous vulnerability scanning services
Explore our full suite of continuous vulnerability assessment services designed for every layer of your security stack.

Web Application Security Scanning
- Simulate real-world attacks with our web app vulnerability scanner to uncover OWASP Top 10, CWE, SANS25, MITRE ATT&CK Framework, and more
- Validate fixes quickly with developer-friendly PoCs and automated rescans
- Leverage ongoing compliance for ISO, SOC 2, PCI DSS, HIPAA, GDPR, and more

API Security Testing
- Discover shadow, zombie, and undocumented APIs to prevent data leaks and unauthorized access
- Run authenticated scans against REST, SOAP, GraphQL, and backend integrations
- Aligns with OWASP API Top 10, PCI DSS, GDPR, SOC 2, GDPR and more

Cloud Security Testing
- Scan AWS, GCP, and Azure for misconfigurations, privilege escalations, and exposed services
- Provide step-by-step remediation for secure multi-cloud operations
- Get continuous compliance for OWASP Kubernetes Top 10, ISO, SOC 2, CIS Benchmarks, PCI DSS, CSA, and more

Continuous Monitoring
- Schedule scans daily, weekly, or monthly for continuous monitoring
- Track emerging CVEs, validate patches, and monitor security posture across updates
- Receive real-time alerts, continuous scans, and expert validation to stay compliant
- Request vetting by experts to ensure accuracy and minimize false positives

Automated Re-scanning
- Verify fixes automatically to ensure vulnerabilities are fully resolved
- Streamline remediation through a single dashboard for scans and rescans
- Save time by re-scanning only updated or fixed components
Specialized Vulnerability Scanning Services
- Lightning Scans: Run a high-level scan addressing basic security vulnerabilities
- Emerging Scans: Detect vulnerabilities associated with emerging threats, such as RegreSSHion, Polyfill, Log4Shell, and Text4Shell
- Full scans: Scans all endpoints, including authenticated areas, within 12–24 hours
- Delta scans: Run incremental scans targeting recent changes in your app, boosting performance and minimizing scan duration





Secure every layer of your digital footprint with Astra Security’s tailored and continuous vulnerability scanner.
Book a DemoAstra Security vs traditional vendors
See how our modern approach to continuous vulnerability management services outpaces traditional vendor models.
Experience the Astra Security difference: faster, smarter, compliance-ready pentesting.
Pentesting as a service, tailored for your industry
Continuous penetration testing and compliance mapping services built for ISO, SOC 2, HIPAA, PCI DSS, and more.

- Secure financial systems and payment workflows from logic flaws
- Deliver actionable fixes and maintain PCI DSS, ISO 27001, SOC 2, DORA compliance, and more
- Standards: OWASP, PTES, CVSS

- Protect patient data and secure APIs across web, mobile, and cloud
- Uncover hidden PHI exposures and validate HIPAA, ABHA, and more
- Standards: OWASP, PTES, NIST, CVSS

- Accelerate app security with DevSecOps integration and continuous scans
- Detect vulnerabilities with AI-driven validation and ensure ISO 27001, SOC 2, GDPR compliance and more
- Standards: OWASP, PTES, CVSS, NIST SP 800-115

- Protect customer data and secure payment flows from BOLA/IDOR risks
- Empower developers with guided remediation and PCI DSS, ISO 27001, SOC 2 compliance and more
- Standards: OWASP, PTES, CVSS

- Fortify cloud, container, and on-prem systems with authenticated tests
- Monitor and validate vulnerabilities to prevent downtime; comply with NIST, ISO 27001, SOC 2, CREST, Cert-In, and more
- Standards: OWASP, PTES, NIST, CVSS

- Discover shadow APIs and secure cloud services
- Deliver fast, developer-friendly fixes; ensure GDPR, ISO 27001, SOC 2 compliance
- Standards: OWASP, PTES, CVSS
Simulate real-world attacks, uncover hidden risks, and strengthen your defenses with expert-led continuous vulnerability scanning services for just $69.
Start TrialOur pentesters? World class, certified & contributors to top security projects
We find the bugs before the bad guys do
Our team stays ahead of the curve in the ever-evolving world of web security

.avif)
.avif)
.avif)





Stay compliant throughout the year
Understand our industry-specific pentests as a service plans designed to meet your compliance, scale, and security needs.
- Get compliance-ready year-round for ISO 27001, SOC 2, GDPR, HIPAA, PCI DSS, CREST, CERT-In, CIS Controls, NIST, & more
- Receive actionable insights from continuous pentesting and expert-led remediation guidance
- Track compliance progress with the Astra Security Compliance View, providing executive-friendly and technical views


- Maintain audit-ready reports without manual effort
- Reduce risk exposure with real-time detection and validation
- Prioritize remediation based on business impact and compliance requirements
- Demonstrate security maturity to clients, regulators, and internal stakeholders


Frequently asked questions
What is continuous vulnerability scanning?
Continuous vulnerability scanning is an automated, expert-validated process that detects security weaknesses across web, API, and cloud environments in real time, providing verified findings, prioritization, and remediation guidance to reduce risk and maintain compliance.
How does continuous vulnerability scanning work?
It identifies in-scope systems, sets up authentication, runs automated scans, scores risks, delivers remediation steps, and validates fixes with recurring scans, combining AI-powered detection and expert reviews for accurate, actionable security intelligence.
Why is continuous scanning important for organizations?
Continuous vulnerability scanning detects vulnerabilities as they emerge, prevents exploit risks, supports compliance, reduces false positives, and enables rapid remediation, ensuring organizations maintain a resilient, audit-ready security posture
How often should vulnerability scans be conducted?
As the name suggests, scan frequency should ideally be continuous, but it also depends on application size, business needs, and industry requirements. Delta, emerging, or lightning scans can run daily for rapid coverage, full scans are recommended weekly or bi-weekly, and one vetted scan per month or quarter ensures deep, zero-false-positive validation.
How much does continuous vulnerability scanning cost?
Astra Security’s continuous vulnerability scanning plans start at just $69 per month, with trial options available for as low as $7. All plans include comprehensive vulnerability scanning, detailed reports, and continuous support, offering businesses an affordable, scalable, and reliable way to strengthen their security posture
Does it help with compliance monitoring?
Yes, continuous scanning maps findings to standards like ISO 27001, PCI DSS, SOC 2, HIPAA, GDPR, and more to generate audit-ready reports, track remediation progress, validate fixes, and provide executive-friendly dashboards, ensuring your organization stays compliant year-round while demonstrating security maturity to regulators and clients. An annual pentest report is still required in addition to the above to achieve and renew compliance certificates.











