Cybersecurity Assessment Services For A Safer Tomorrow
Opt Astra Security’s intelligent cybersecurity assessment services to monitor your assets in a rapidly changing cyber environment continuously.











Astra's 7-Step Pentest Process
Comprehensive security assessment from start to finish
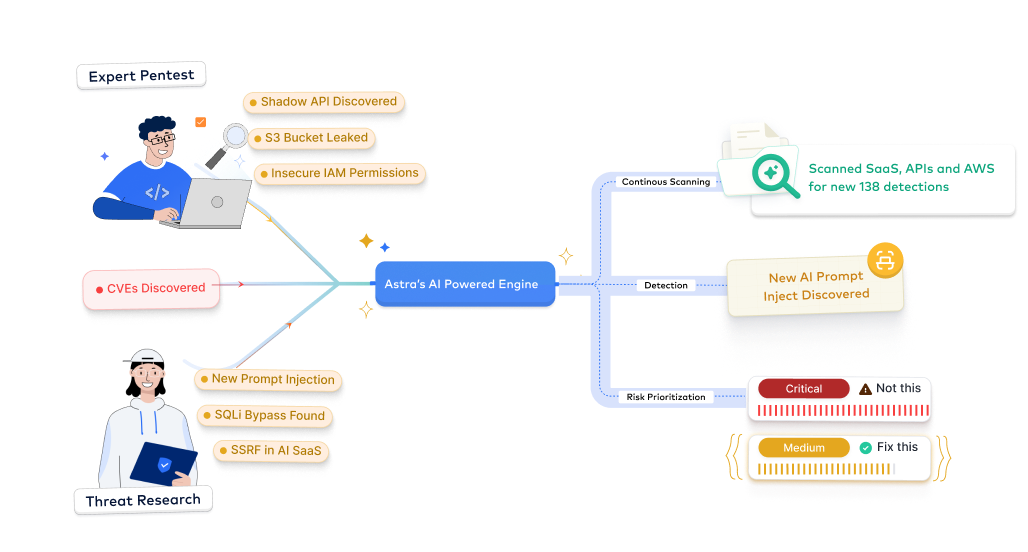
Astra's hacker-style pentest process combines years of pentester experience, cutting-edge AI, and deep knowledge of industry standards. Our battle-tested approach ensures comprehensive coverage, uncovering vulnerabilities that others miss.
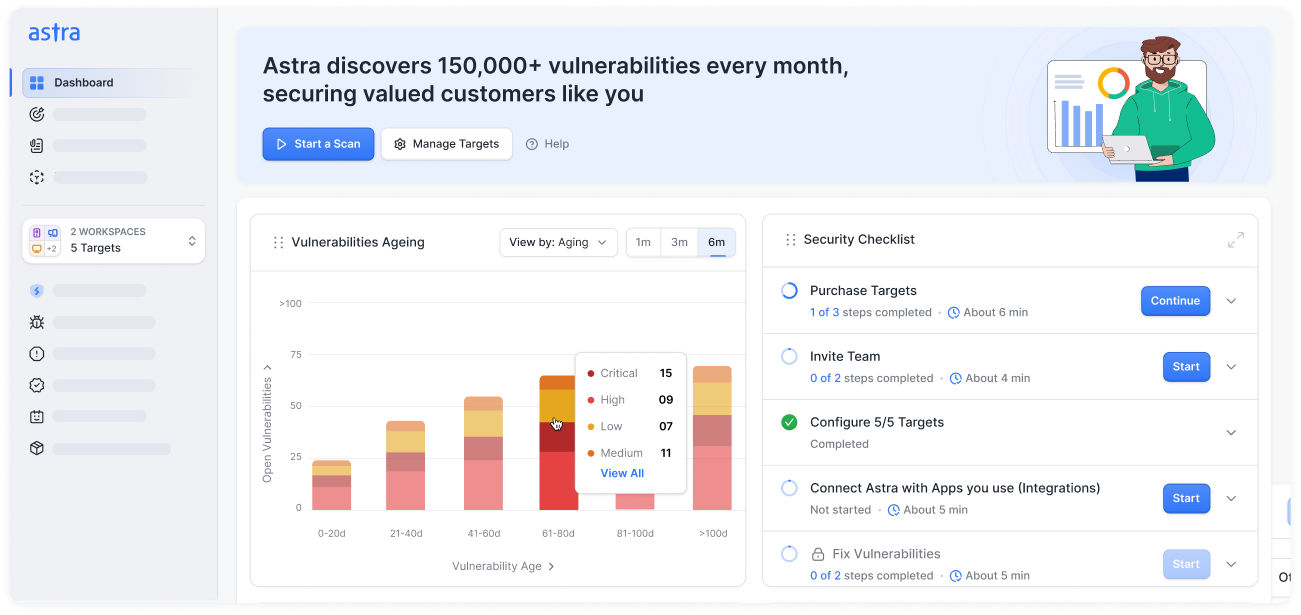
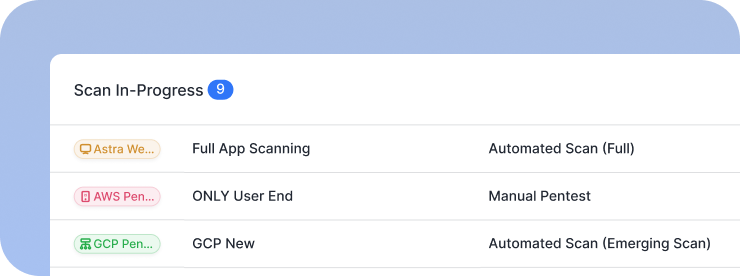
Continuous Penetration Testing


Comprehensive Vulnerability Assessment
Malware Scanner


Scan Behind Logins
Vetted Scans


From startups to fortune companies,
1000+ companies trust Astra












































.webp)















Experience the Astra Security difference: faster, smarter, compliance-ready pentesting.
Pentesting as a service, tailored for your industry
Continuous penetration testing and compliance mapping services built for ISO, SOC 2, HIPAA, PCI DSS, and more.

- Secure financial systems and payment workflows from logic flaws
- Deliver actionable fixes and maintain PCI DSS, ISO 27001, SOC 2, DORA compliance, and more
- Standards: OWASP, PTES, CVSS

- Protect patient data and secure APIs across web, mobile, and cloud
- Uncover hidden PHI exposures and validate HIPAA, ABHA, and more
- Standards: OWASP, PTES, NIST, CVSS

- Accelerate app security with DevSecOps integration and continuous scans
- Detect vulnerabilities with AI-driven validation and ensure ISO 27001, SOC 2, GDPR compliance and more
- Standards: OWASP, PTES, CVSS, NIST SP 800-115

- Protect customer data and secure payment flows from BOLA/IDOR risks
- Empower developers with guided remediation and PCI DSS, ISO 27001, SOC 2 compliance and more
- Standards: OWASP, PTES, CVSS

- Fortify cloud, container, and on-prem systems with authenticated tests
- Monitor and validate vulnerabilities to prevent downtime; comply with NIST, ISO 27001, SOC 2, CREST, Cert-In, and more
- Standards: OWASP, PTES, NIST, CVSS

- Discover shadow APIs and secure cloud services
- Deliver fast, developer-friendly fixes; ensure GDPR, ISO 27001, SOC 2 compliance
- Standards: OWASP, PTES, CVSS
Our pentesters? World class, certified & contributors to top security projects
We find the bugs before the bad guys do
Our team stays ahead of the curve in the ever-evolving world of web security

.avif)
.avif)
.avif)





Stay compliant throughout the year
Understand our industry-specific pentests as a service plans designed to meet your compliance, scale, and security needs.
- Get compliance-ready year-round for ISO 27001, SOC 2, GDPR, HIPAA, PCI DSS, CREST, CERT-In, CIS Controls, NIST, & more
- Receive actionable insights from continuous pentesting and expert-led remediation guidance
- Track compliance progress with the Astra Security Compliance View, providing executive-friendly and technical views


- Maintain audit-ready reports without manual effort
- Reduce risk exposure with real-time detection and validation
- Prioritize remediation based on business impact and compliance requirements
- Demonstrate security maturity to clients, regulators, and internal stakeholders


Frequently asked questions
What are the benefits of employing Astra's cybersecurity assessment services?
The following are the benefits of employing Astra Security's cybersecurity solutions:
1. Identify and fix security flaws in your website.
2. Penetration testing emulates real-life attack scenarios and helps in mitigating risks.
3. Help in achieving certain compliance requirements and avoid hefty penalties for non-compliance.
How does Astra help with vulnerability remediation?
Astra provides remediation assistance in the following ways:
1. Dashboard allows contextual collaboration between expert pentesters and developers of customer organization for efficient remediation.
2. Comment boxes directly underneath every listed vulnerability so that you can clear your queries immediately.
3. Actionable VAPT reports with easy-to-follow remediation steps and with risk scores based on CVSS scores and contextual data for prioritization of fixes.
4. Customer service is available 24*7 through emails, phone calls, and chats.
What is contained in Astra's cybersecurity services?
The cybersecurity assessment services provided by Astra Security ensure holistic safety for your assets. It includes:
1. Continuous pentests
2. In-depth vulnerability assessments
3. Compliance-specific scans
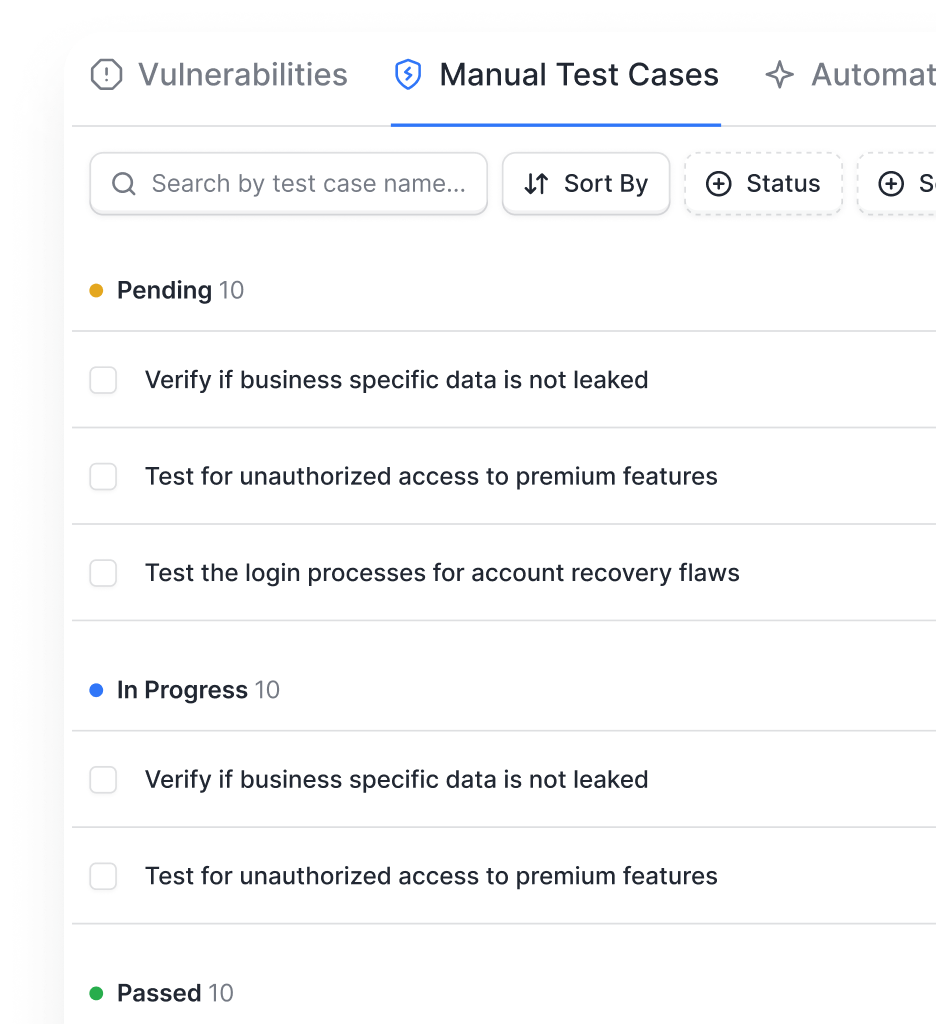
4. Scan Behind Logins
5. Vetted scans and more
Can I request a re-scan to check if the vulnerability is patched?
Yes, Astra Security's cybersecurity assessment services include vulnerability assessments and penetration tests. The successful remediation of the vulnerabilities identified is verified with the help of mandatory unlimited re-scans.
How do scans behind logins work?
Astra's chrome extension comes with a login recorder that records your login credentials seamlessly to carry out authenticated scans without session time-outs.
Why is manual vetting necessary?
Manual vetting of automated vulnerability scan results by expert pentesters can help in the weeding out of pesky false positives. This gives you a completely actionable report with zero false positives for remediation efficiency.