#1 Google Cloud Services Security (Trusted by 1000+ Teams)
Safeguard your Google environment against misconfigurations, identity risks, and evolving threats. Astra’s continuous Google Cloud security services and configuration reviews detect, validate, and help you fix vulnerabilities across your GCP workloads, APIs, and infrastructure.

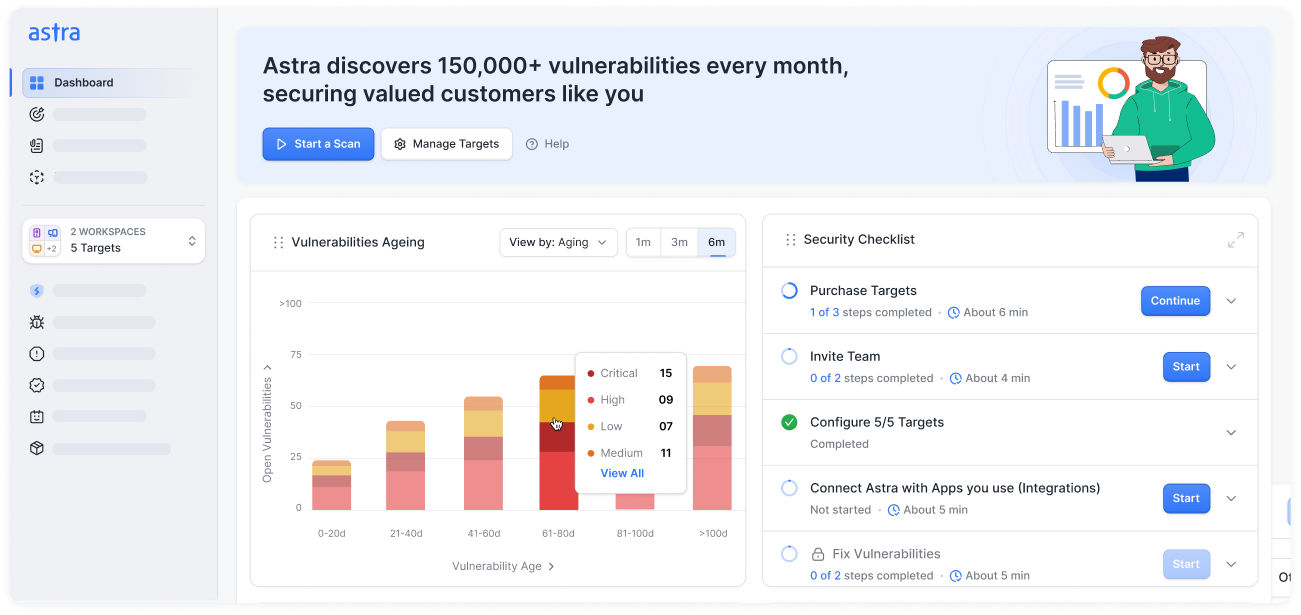










Why choose Astra Security’s Google Cloud Services Security?
Experience continuous, expert-led cloud security built for the GCP ecosystem, with automated monitoring, manual validation, and compliance-ready insights.
- Focus on real misconfigurations and exposure points, not generic scan noise.
- Our experts manually validate cloud findings to eliminate false positives.
- Get contextual PoCs showing real-world exploitability and privilege paths.
- Track verified fixes with automated revalidation scans directly from your Astra dashboard.
- AI-driven analysis identifies privilege escalations, IAM drift, and open storage buckets.
- Adaptive detection logic evolves with GCP’s latest services, APIs, and exploit trends.
- Machine learning models correlate findings with threat intelligence and MITRE ATT&CK tactics.
- Achieve complete visibility across hybrid or multi-cloud deployments.
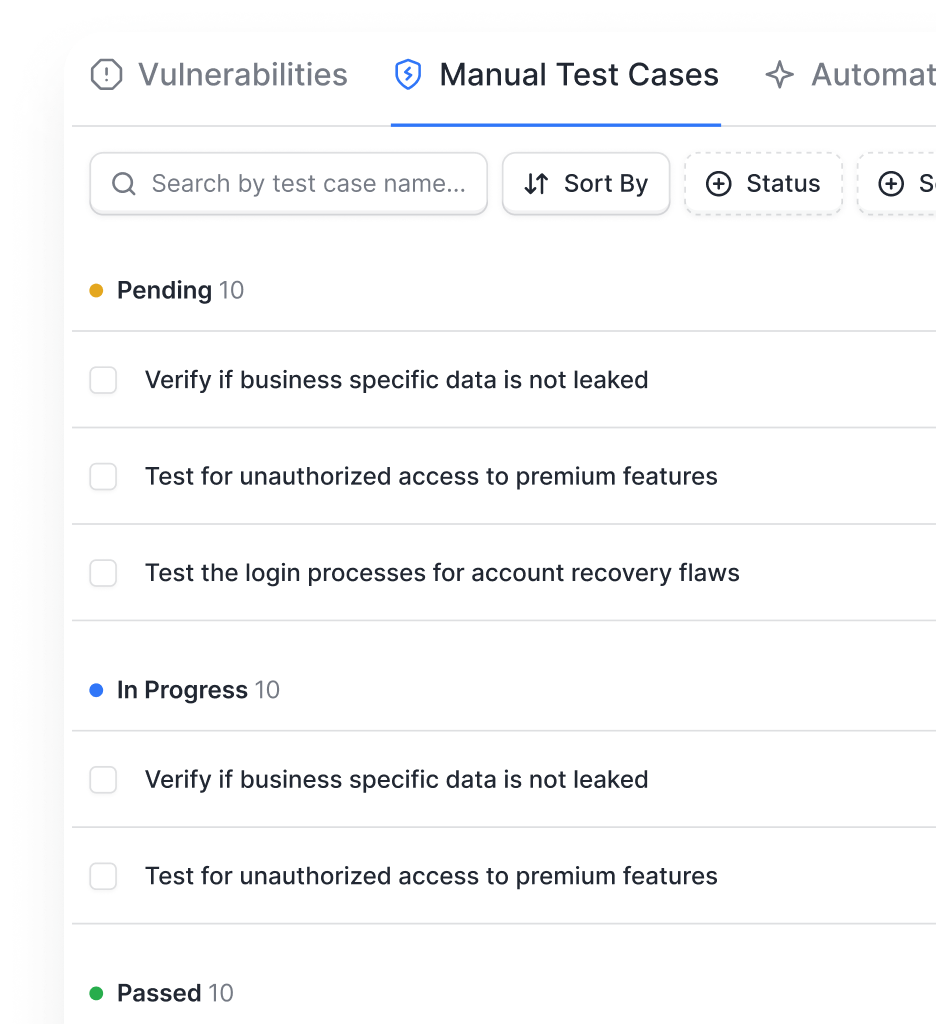
- Combine automated scanning with manual cloud pentesting by certified experts.
- Stay ahead of misconfigurations and policy drift through continuous GCP monitoring.
- Get ongoing vulnerability tracking, retesting, and compliance alignment for ISO, SOC 2, and PCI DSS.
- Cut false positives and achieve measurable ROI through managed cloud accuracy.
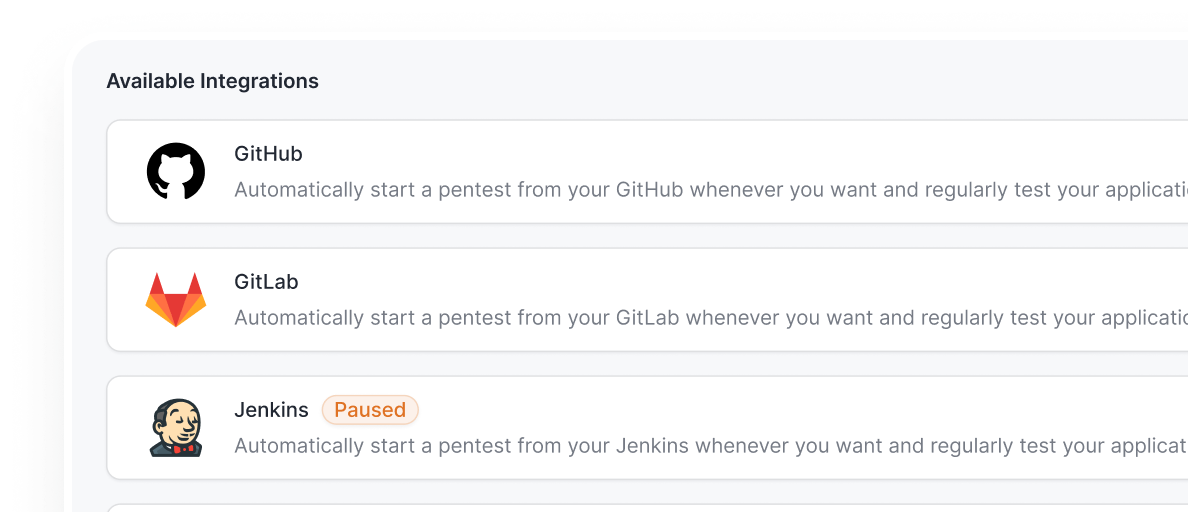
- Integrate GCP security testing into your CI/CD workflows (GitHub, GitLab, Jenkins, Bitbucket & more).
- Automate continuous scans, receive Slack alerts, and create Jira tickets directly from Astra.
- Shorten your mean time to remediate without disrupting cloud deployment cycles.
- Maintain continuous visibility into cloud posture while releasing faster.
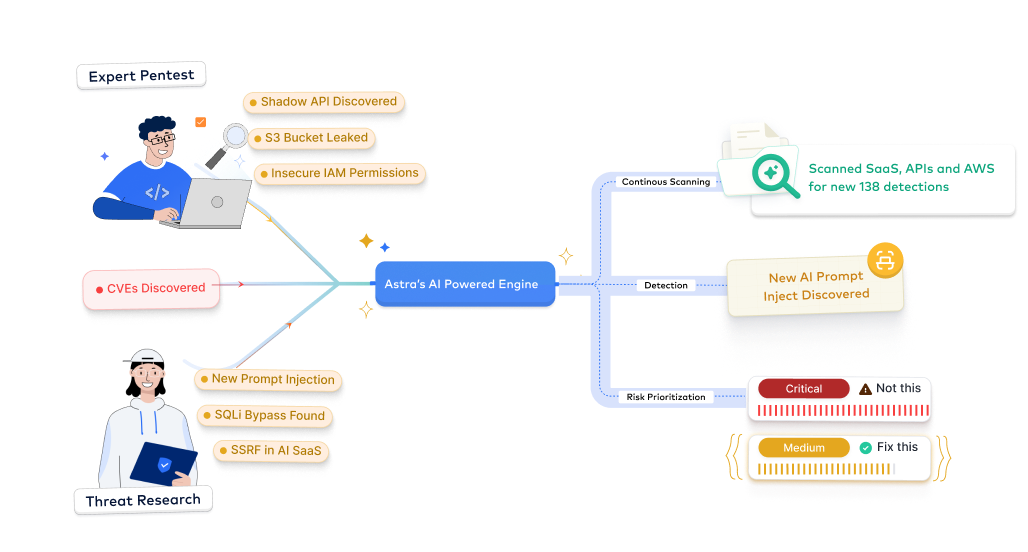
- Generate audit-ready reports mapped to ISO 27001, SOC 2, GDPR, PCI DSS, HIPAA, and NIST frameworks.
- Accelerate GCP certification readiness with expert-led security guidance.
- Demonstrate cloud security maturity to customers, partners, and regulators.
- Turn cloud compliance into a trust and sales advantage.

Secure every workload and API with Astra’s expert-led Google Cloud Services Security, starting at just $5,999.
Start TrialAstra's 7-Step Pentest Process
How our Google Cloud Services Security works
Learn how Astra’s experts secure your Google Cloud infrastructure, from discovery to validation, with continuous monitoring, manual pentesting, and compliance alignment.
Discovery & Access
- Identify and catalog all in-scope cloud assets across your GCP environment
- Establish secure, read-only access using credential-aware scans with verified tokens and programmatic keys
- Define assessment parameters to cover multi-region environments and apps, including GovCloud
- Align the engagement scope with compliance frameworks like SOC2, ISO 27001, and PCI-DSS
Outcome: Build a complete cloud asset inventory with authenticated access for deep security evaluation


Config Posture Review
- Run automated scans using 400+ configuration checks to identify misconfigurations, privilege gaps, and security weaknesses
- Continuously map your configuration against CIS Benchmarks and cloud-specific best practices
- Identify insecure defaults, exposed services, and mismanaged identities in real-time
- Correlate findings with historical data to track posture drift and emerging risks
Outcome: A comprehensive baseline of configuration vulnerabilities and compliance gaps, ready for analysis
Threat-Path Analysis
- Emulate real-world attack vectors to uncover exploitable paths between misconfigs and identities
- Analyze the blast radius of critical findings to understand potential business impact
- Contextually prioritize risks based on exploitability, access level, and compliance relevance
- Map vulnerabilities to specific compliance controls for targeted remediation
Outcome: Identify real-world attack scenarios that could compromise your Google Cloud infrastructure


Manual Validation
- Our security experts manually validate high-severity configuration findings to ensure accuracy and eliminate false positives
- Conduct in-depth reviews of configuration settings, IAM policies, and access controls to verify adherence to security best practices
- Receive expert-validated findings, with a comprehensive understanding of configuration issues and their potential business impact
Outcome: Receive expert-validated, exploitable vulnerabilities with verified business impact assessment
Reporting & Handoff
- Receive a detailed report with dev-friendly steps to fix each vulnerability, complete with code snippets
- Get compliance-mapped evidence for SOC2, ISO 27001, and PCI-DSS in an audit-ready format
- Access interactive dashboards for live vulnerability tracking and team collaboration
- Schedule a handoff call with our experts for walkthroughs and remediation planning
Outcome: Gain actionable insights with dev-friendly fixes and compliance-ready documentation


Rescan & Attestation
- Conduct detailed manual retests or get instant, targeted rescans of individual vulnerabilities to validate fixes without full scans
- Perform final comprehensive rescans to ensure all identified risks are remediated
- Capture time-stamped validation evidence for audit trails and certification renewals
- Issue a verifiable certificate of GCP cloud security attesting to your hardened posture.
Outcome: Achieve verified remediation with continuous cloud security monitoring and compliance attestation
From startups to fortune companies,
1000+ companies trust Astra












































.webp)





Protect your Google Cloud environment from evolving threats with Astra’s expert-led Cloud Security Testing Services.
Request Pentesting ServicesTypes of Google Cloud security services
Explore Astra’s end-to-end Google Cloud security testing services built to safeguard your workloads, apps, and data.

Cloud Infra Configuration Review
- Scan GCP for security misconfigs, insecure defaults, and privilege escalations
- Continuously monitor for posture drift and mismanaged identities across multi-region environments
- Compliance-ready for CIS Benchmarks, SOC 2, ISO 27001, NIST, and PCI-DSS

Kubernetes & Container Security Assessment
- Probe container registries, orchestration layers (like EKS & AKS), and pods for orchestration risks
- Uncover vulnerabilities in cluster configs, network policies, and secrets management
- Aligns with OWASP Kubernetes Top 10, CIS Benchmarks, and SOC 2 controls

Continuous Vulnerability Scanning Application Penetration Testing
- Detects and validates misconfigurations and IAM risks across Google Cloud
- Run 400+ cloud-specific checks across configurations, permissions, and services, detecting misconfigs, excessive privileges, and compliance gaps
- Compliance-mapped for PCI-DSS, ISO 27001, SOC 2, and GDPR

Cloud API Security
- Discover and test shadow, undocumented, and public-facing APIs for data exposure risks
- Run authenticated, in-depth scans against REST, GraphQL, and serverless API endpoints
- Aligns with OWASP API Security Top 10, PCI-DSS, and SOC 2 compliance requirements

Serverless Function Security
- Assess serverless architectures for insecure deployment and event-injection flaws
- Identify over-permissive roles, cold-start attacks, and improper data handling
- Provide targeted remediation for function-specific risks in a serverless environment
Cloud Storage & Database Security Review
- Audit cloud storage buckets and databases (CosmosDB) for public exposure and weak encryption.
- Validate access controls and data-in-transit policies to prevent mass data leaks.
- Compliance-ready for data protection standards in PCI-DSS, HIPAA, and GDPR.





Strengthen your Google Cloud ecosystem from IAM to workloads with Astra’s full-suite security testing services.
Book a DemoAstra Security vs traditional vendors
See how Astra’s modern approach to Google Cloud security testing outpaces traditional vendor models.
Experience the Astra Security difference: faster, smarter, compliance-ready pentesting.
Pentesting as a service, tailored for your industry
Continuous penetration testing and compliance mapping services built for ISO, SOC 2, HIPAA, PCI DSS, and more.

- Secure financial systems and payment workflows from logic flaws
- Deliver actionable fixes and maintain PCI DSS, ISO 27001, SOC 2, DORA compliance, and more
- Standards: OWASP, PTES, CVSS

- Protect patient data and secure APIs across web, mobile, and cloud
- Uncover hidden PHI exposures and validate HIPAA, ABHA, and more
- Standards: OWASP, PTES, NIST, CVSS

- Accelerate app security with DevSecOps integration and continuous scans
- Detect vulnerabilities with AI-driven validation and ensure ISO 27001, SOC 2, GDPR compliance and more
- Standards: OWASP, PTES, CVSS, NIST SP 800-115

- Protect customer data and secure payment flows from BOLA/IDOR risks
- Empower developers with guided remediation and PCI DSS, ISO 27001, SOC 2 compliance and more
- Standards: OWASP, PTES, CVSS

- Fortify cloud, container, and on-prem systems with authenticated tests
- Monitor and validate vulnerabilities to prevent downtime; comply with NIST, ISO 27001, SOC 2, CREST, Cert-In, and more
- Standards: OWASP, PTES, NIST, CVSS

- Discover shadow APIs and secure cloud services
- Deliver fast, developer-friendly fixes; ensure GDPR, ISO 27001, SOC 2 compliance
- Standards: OWASP, PTES, CVSS
Secure every workload and API with Astra’s expert-led Google Cloud Services Security, starting at just $5,999.
Start TrialOur pentesters? World class, certified & contributors to top security projects
We find the bugs before the bad guys do
Our team stays ahead of the curve in the ever-evolving world of web security

.avif)
.avif)
.avif)





Stay compliant throughout the year
Understand our industry-specific pentests as a service plans designed to meet your compliance, scale, and security needs.
- Get compliance-ready year-round for ISO 27001, SOC 2, GDPR, HIPAA, PCI DSS, CREST, CERT-In, CIS Controls, NIST, & more
- Receive actionable insights from continuous pentesting and expert-led remediation guidance
- Track compliance progress with the Astra Security Compliance View, providing executive-friendly and technical views

- Continuously monitor GCP workloads, APIs, and configurations for new CVEs and privilege misuses.
- Validate vulnerabilities in real time using automated reconnaissance and expert triage.
- Track remediation progress and risk scores in Astra’s Vulnerability View for smarter decisions.

- Maintain audit-ready reports without manual effort
- Reduce risk exposure with real-time detection and validation
- Prioritize remediation based on business impact and compliance requirements
- Demonstrate security maturity to clients, regulators, and internal stakeholders


Frequently asked questions
What is Google Cloud security testing?
Google Cloud security configuration reviews assess your GCP-hosted applications, workloads, and configurations to identify vulnerabilities, misconfigurations, or IAM flaws that could be exploited by attackers. It ensures your cloud environment aligns with leading security and compliance benchmarks.
How is Google Cloud security testing different from regular penetration testing?
Traditional pentesting focuses on exploiting system vulnerabilities, while GCP security configuration reviews evaluate both infrastructure and service-level risks, including IAM policies, network exposure, and storage permissions. It provides a holistic view of your cloud’s security posture.
Why is Google Cloud security testing important?
It helps prevent data exposure, misconfigured storage buckets, and privilege escalation attacks. By identifying weaknesses before attackers do, you protect your cloud assets, maintain uptime, and meet compliance obligations with confidence.
How often should my organization perform Google Cloud security testing?
It’s best to review quarterly or after major deployments, configuration changes, or new workload launches. Continuous validation ensures that your GCP setup remains secure against evolving threats.
Does Astra Security offer testing for all GCP services?
Yes. Astra’s coverage includes Compute Engine, Kubernetes Engine, App Engine, Cloud Storage, IAM, APIs, and networking components, all tested under configuration reviews and mapped to global compliance standards.
How does Astra’s Google Cloud testing differ from others?
Astra combines manual expertise with AI-driven automation, providing continuous monitoring, Jira/Slack integrations, patch validation, and compliance alignment; far beyond one-time vendor assessments.











