#1 Red Team Assessment Services (Trusted by 1000+ Teams)
Simulate advanced, real-world attacker campaigns against your people, processes, and technology. Astra’s red team assessment services combine adversary simulation, human-led attack chains, and business-impact reporting to expose gaps, harden controls, and improve incident response readiness.

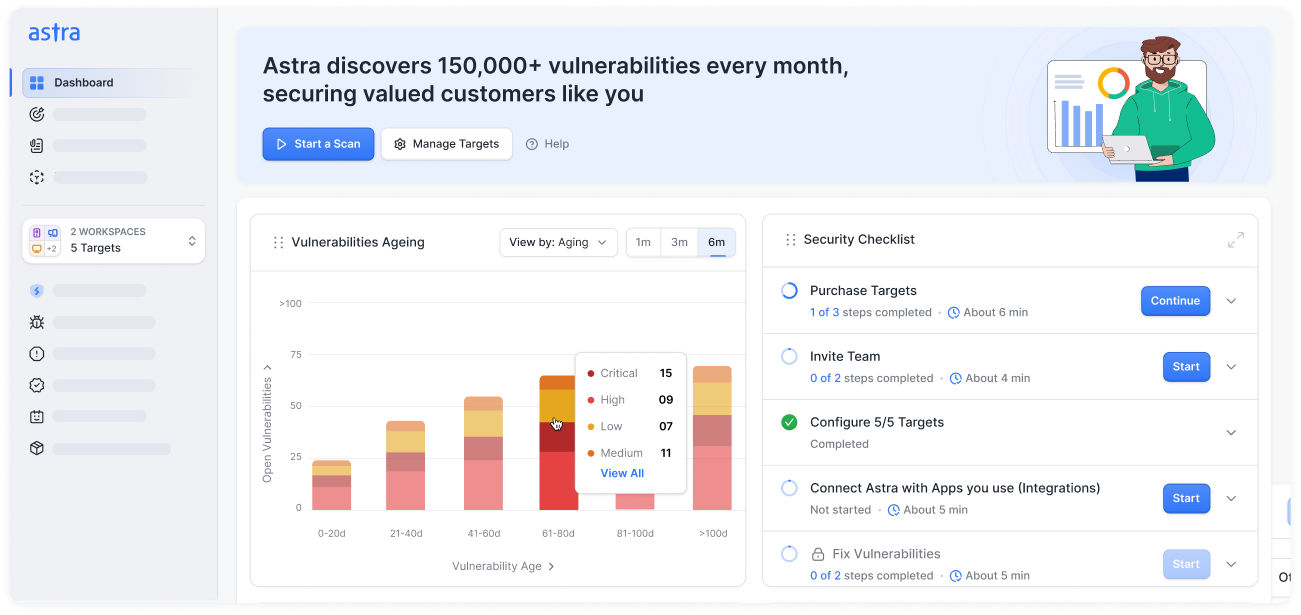










Why choose Astra Security's red team assessment services?
Experience our red team plans built for modern security and SOC teams with expert-driven adversary simulations, contextual intelligence, and continuous maturity-building at scale.
- Focus on real attack paths and validated impact, not noise or scanner outputs
- Our experts verify exploitability and business impact so your team prioritizes correctly
- Mark verified attack chains once to skip duplicate work in future engagements
- Get executive-ready summaries and technical PoCs for rapid decision-making
- Cut manual effort; our threat models and operator playbooks adapt to your environment and industry
- Context-aware analysis improves accuracy and maps findings to likely attacker objectives
- Leverage evolving threat intelligence from real-world campaigns to simulate high-fidelity attacks
- Scale adversary simulation coverage without growing headcount
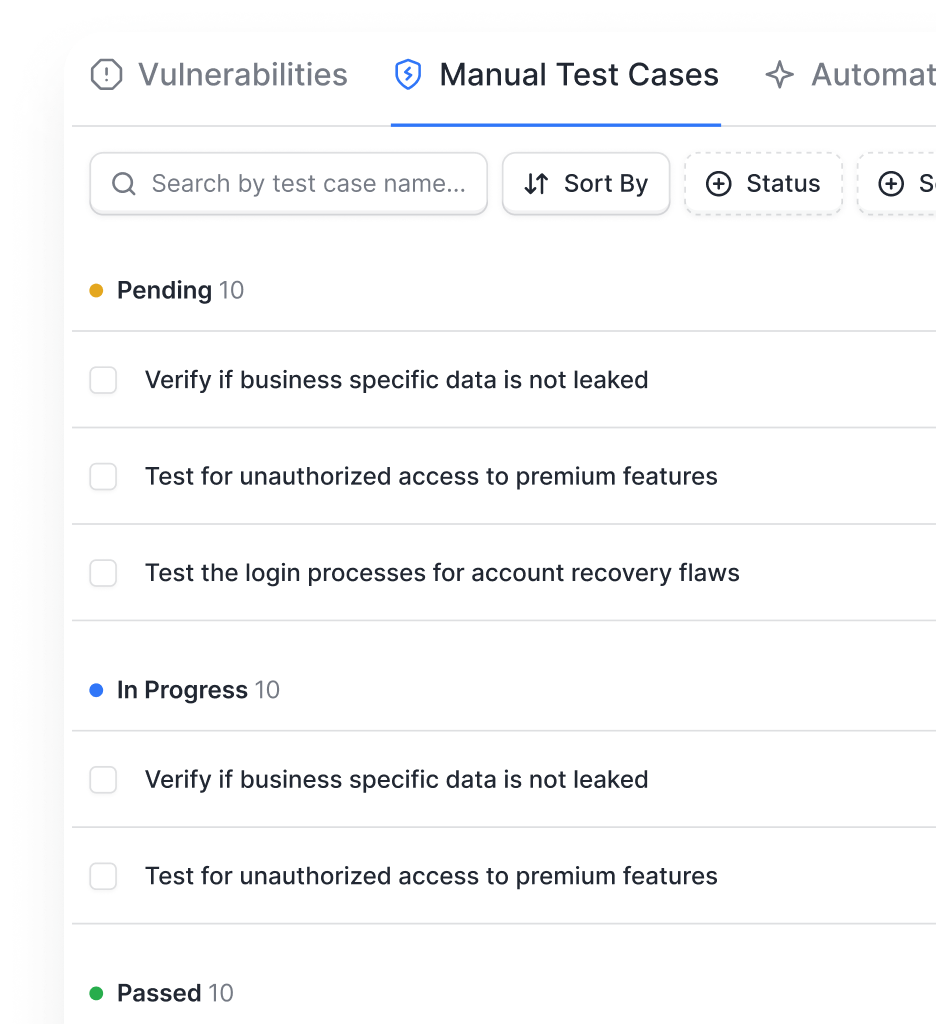
- Execute full-scope red team operations across external, internal, cloud, and identity surfaces
- Avoid alert fatigue with attacker-validated findings and clear escalation paths for incident response teams
- Stay audit-ready with detailed reports, validated fixes, and targeted follow-up exercises
- Reduce remediation cost and effort with prioritized, attacker-context remediation guidance
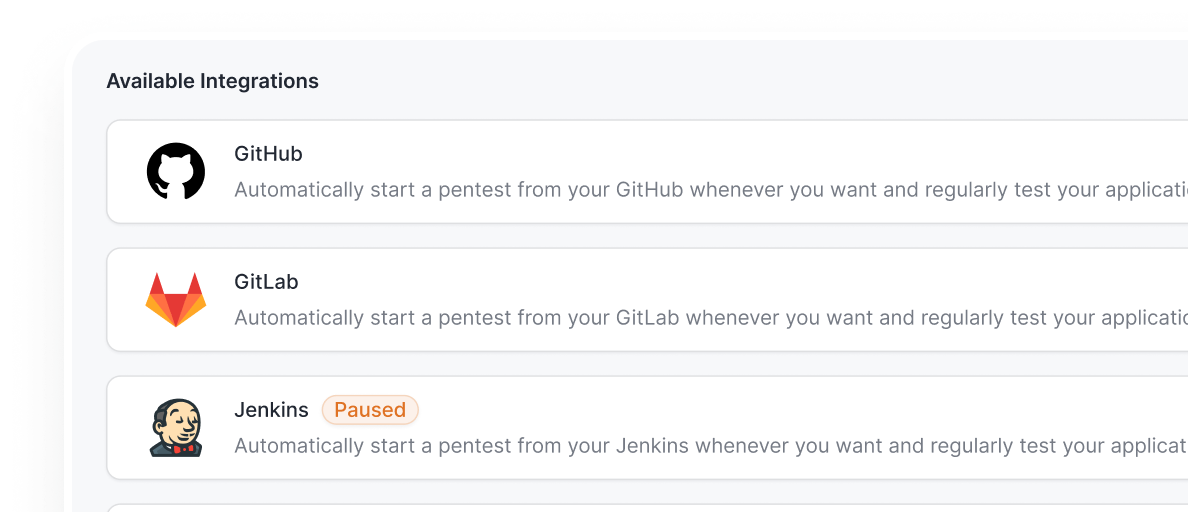
- Integrate red team outputs into SOC, SIEM, and incident response playbooks with zero disruption
- Automate alerting, ticketing, and detection tuning to convert findings into improved telemetry and signatures
- Shorten the mean time to detect and respond with attacker-sourced detection requirements
- Maintain business continuity while improving your defensive posture
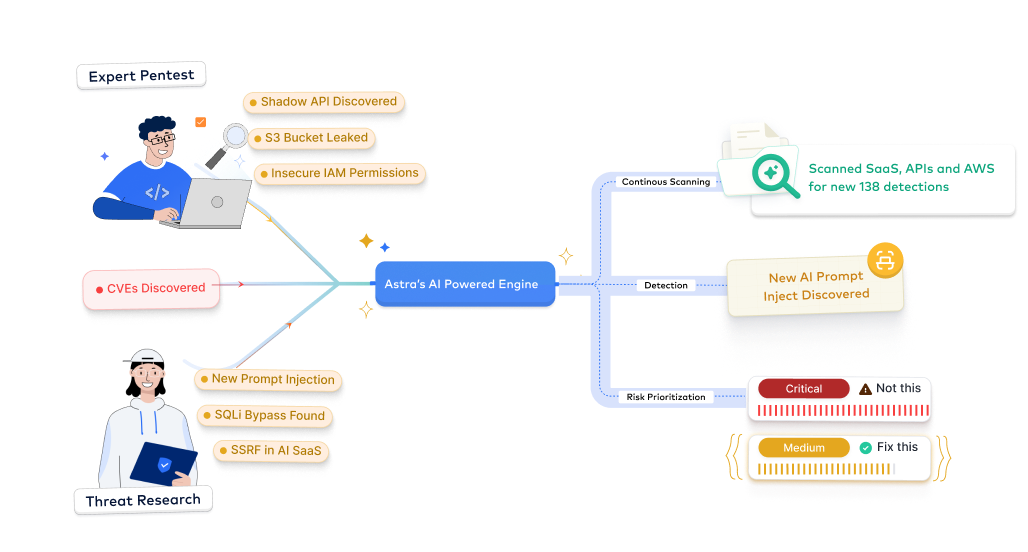
- Generate audit-ready reports for ISO, PCI, SOC 2, HIPAA, GDPR, NIST, and more
- Accelerate certification with simplified expert-led guidance
- Demonstrate security maturity to shorten sales cycles
- Turn adversary simulation readiness into a measurable security maturity advantage

Simulate real-world cyberattacks, test your incident response, and strengthen defenses with expert-led Red Team assessment services for just $5,999.
Start TrialAstra's 7-Step Pentest Process
How our red team assessment services work
Learn how our team delivers high-fidelity adversary simulations that drive measurable security improvements.
Discovery & Scoping
- Identify all in-scope assets: external footprint, internal networks, identity providers, cloud environments, and human targets
- Define mission objectives, rules of engagement, and legal/safety guardrails to align expectations
- Map scope to relevant compliance and risk requirements (SOC 2, ISO 27001, NIST)
- Personalized setup and ROE to maintain visibility and safety throughout the engagement.
Outcome: Agree on a mission scope, success criteria, and a roadmap for detection & remediation improvements


Authentication Setup
- Establish secure access channels and credentials required for controlled simulations, from limited network entry points to employee-facing phishing exercises.
- Integrate red team accounts, testing environments, and command-and-control channels to conduct multi-vector operations safely.
- Ensure testing is isolated and coordinated to avoid production impact while maintaining real-world conditions.
- Create standardized access and configuration templates for recurring red or purple team assessments.
Outcome: Enable full-depth adversarial testing without disrupting live operations.
Automated Baseline
- Leverage Astra’s automation engine to map vulnerabilities, exposed services, misconfigurations, and weak credentials across internal and external surfaces.
- Correlate findings from reconnaissance, scanning, and OSINT collection to identify potential footholds.
- Combine automated insights with previous red team data for historical visibility and evolving risk tracking.
- Generate baseline intelligence that informs manual simulation strategy and future defensive improvements.
Outcome: Gain a comprehensive, real-time baseline of exploitable weaknesses across your organization.


Risk Scoring
- Astra’s red team experts manually execute targeted simulations, including social engineering, phishing, privilege escalation, lateral movement, and data exfiltration, to mimic real attackers.
- Each action is validated, documented, and scored for business and operational impact.
- Use contextualized CVSS scoring, mapped to MITRE ATT&CK, to prioritize remediation by exploitability and potential damage.
- Provide both technical and executive-level summaries for clear decision-making.
Outcome: Receive validated, high-impact findings that reflect real-world attack potential and readiness gaps.
Remediation Support
- Deliver detailed, step-by-step remediation guidance validated by Astra’s offensive security experts.
- Include PoCs, configuration fixes, and defensive control tuning for faster resolution and resilience enhancement.
- Collaborate directly with your blue team or SOC to verify fix effectiveness and strengthen detection capabilities.
- Provide full documentation aligned with audit and compliance reporting standards.
Outcome: Achieve faster, verified fixes and build stronger internal defenses against similar future threats.


Re-Scan & Validate
- Perform targeted retests to confirm remediation effectiveness and ensure threat coverage closure.
- Schedule recurring red team or purple team exercises to test evolving defenses against advanced threat simulations.
- Capture evidence of improvement for internal reviews, compliance, and board-level reporting.
- Maintain a living, validated security baseline that demonstrates measurable security maturity over time.
Outcome: Secure a verified, evidence-backed record of your organization’s resilience to real-world threats.
From startups to fortune companies,
1000+ companies trust Astra












































.webp)





Experience attacker-validated findings and actionable detection guidance with Astra’s red team assessments.
Request Pentesting ServicesTypes of red team assessment services
Explore our suite of red team services designed to test people, processes, and technology across the enterprise.

External Network Penetration Assessments
- Simulate real-world adversarial attacks on your external assets and infrastructure.
- Identify exploitable entry points across servers, domains, and exposed services.
- Uncover weaknesses in patching, firewalls, and internet-facing systems before attackers do.

Internal Network Compromise Assessments
- Test how your internal environment holds up once an attacker breaches the perimeter.
- Simulate attempts at privilege escalation, lateral movement, and data exfiltration.
- Evaluate segmentation, detection, and response mechanisms within corporate networks.

Social Engineering & Human Layer Testing
- Assess employee awareness and response to targeted phishing, vishing, and impersonation campaigns.
- Identify behavioral and procedural vulnerabilities that attackers could exploit.
- Provide training insights and data-driven recommendations to improve human resilience.

Application & Cloud Exploitation Assessments
- Test web, mobile, and cloud applications for vulnerabilities that could enable real-world compromise.
- Simulate chained attacks between application flaws, misconfigured IAM roles, and cloud exposures.
- Ensure compliance alignment with OWASP Top 10, SANS 25, and CIS Benchmarks.

Physical Intrusion Simulations
- Evaluate physical security posture by simulating controlled break-ins, tailgating, or badge cloning.
- Assess access controls, surveillance coverage, and incident response readiness.
- Provide actionable strategies to improve physical and cyber-physical security synergy.
Purple Team Exercises
- Collaborate with your blue team to test and strengthen detection and response capabilities.
- Simulate real-time attack chains mapped to the MITRE ATT&CK framework.
- Generate insights to refine monitoring rules, alert tuning, and incident playbooks.





Simulate real-world breaches and build true cyber resilience with Astra’s Red Team Assessment Services.
Book a DemoAstra Security vs traditional vendors
See how our adversary-centric approach outpaces traditional security assessments.
Experience the Astra Security difference: faster, smarter, compliance-ready pentesting.
Pentesting as a service, tailored for your industry
Continuous penetration testing and compliance mapping services built for ISO, SOC 2, HIPAA, PCI DSS, and more.

- Secure financial systems and payment workflows from logic flaws
- Deliver actionable fixes and maintain PCI DSS, ISO 27001, SOC 2, DORA compliance, and more
- Standards: OWASP, PTES, CVSS

- Protect patient data and secure APIs across web, mobile, and cloud
- Uncover hidden PHI exposures and validate HIPAA, ABHA, and more
- Standards: OWASP, PTES, NIST, CVSS

- Accelerate app security with DevSecOps integration and continuous scans
- Detect vulnerabilities with AI-driven validation and ensure ISO 27001, SOC 2, GDPR compliance and more
- Standards: OWASP, PTES, CVSS, NIST SP 800-115

- Protect customer data and secure payment flows from BOLA/IDOR risks
- Empower developers with guided remediation and PCI DSS, ISO 27001, SOC 2 compliance and more
- Standards: OWASP, PTES, CVSS

- Fortify cloud, container, and on-prem systems with authenticated tests
- Monitor and validate vulnerabilities to prevent downtime; comply with NIST, ISO 27001, SOC 2, CREST, Cert-In, and more
- Standards: OWASP, PTES, NIST, CVSS

- Discover shadow APIs and secure cloud services
- Deliver fast, developer-friendly fixes; ensure GDPR, ISO 27001, SOC 2 compliance
- Standards: OWASP, PTES, CVSS
Simulate real-world cyberattacks, test your incident response, and strengthen defenses with expert-led Red Team assessment services for just $5,999.
Start TrialOur pentesters? World class, certified & contributors to top security projects
We find the bugs before the bad guys do
Our team stays ahead of the curve in the ever-evolving world of web security

.avif)
.avif)
.avif)





Stay compliant throughout the year
Understand our industry-specific pentests as a service plans designed to meet your compliance, scale, and security needs.
- Get compliance-ready year-round for ISO 27001, SOC 2, GDPR, HIPAA, PCI DSS, CREST, CERT-In, CIS Controls, NIST, & more
- Receive actionable insights from continuous pentesting and expert-led remediation guidance
- Track compliance progress with the Astra Security Compliance View, providing executive-friendly and technical views


- Maintain audit-ready reports without manual effort
- Reduce risk exposure with real-time detection and validation
- Prioritize remediation based on business impact and compliance requirements
- Demonstrate security maturity to clients, regulators, and internal stakeholders


Frequently asked questions
What is a red team assessment service?
A red team assessment simulates realistic attacker campaigns across technical and human attack surfaces: testing detection, response, and business impact. It reveals not just vulnerabilities, but how attackers could chain them to reach critical assets.
What are the benefits of red team assessments?
They validate your detection and response posture, expose gaps in process and telemetry, reduce attacker dwell time, and provide evidence for compliance and board reporting.
How much does a red team assessment cost?
Costs vary by scope, complexity, and duration. Astra offers transparent pricing that scales with target breadth and engagement depth. Baseline adversary simulations begin at market-competitive rates; custom enterprise engagements are quoted after scoping.
Can I get a custom red team engagement tailored to my environment?
Yes. We scope exercises to target your critical assets, business-impact scenarios, and regulatory requirements, ensuring relevance and measurable outcomes.
Will a red team assessment help with compliance requirements?
Yes. Red team results are mapped to compliance frameworks (SOC 2, ISO 27001, NIST) and provide auditable evidence that helps with certification and regulator communications.
How fast can you deliver results?
Timelines depend on scope. Short, focused engagements (e.g., external compromise simulations) can be completed quickly; full-scope adversary emulations are scoped with clear milestones and delivery windows.











