Red team services to test & strengthen your security
Real-world attack simulations by certified experts. Test your defenses against advanced adversaries & uncover blind spots.

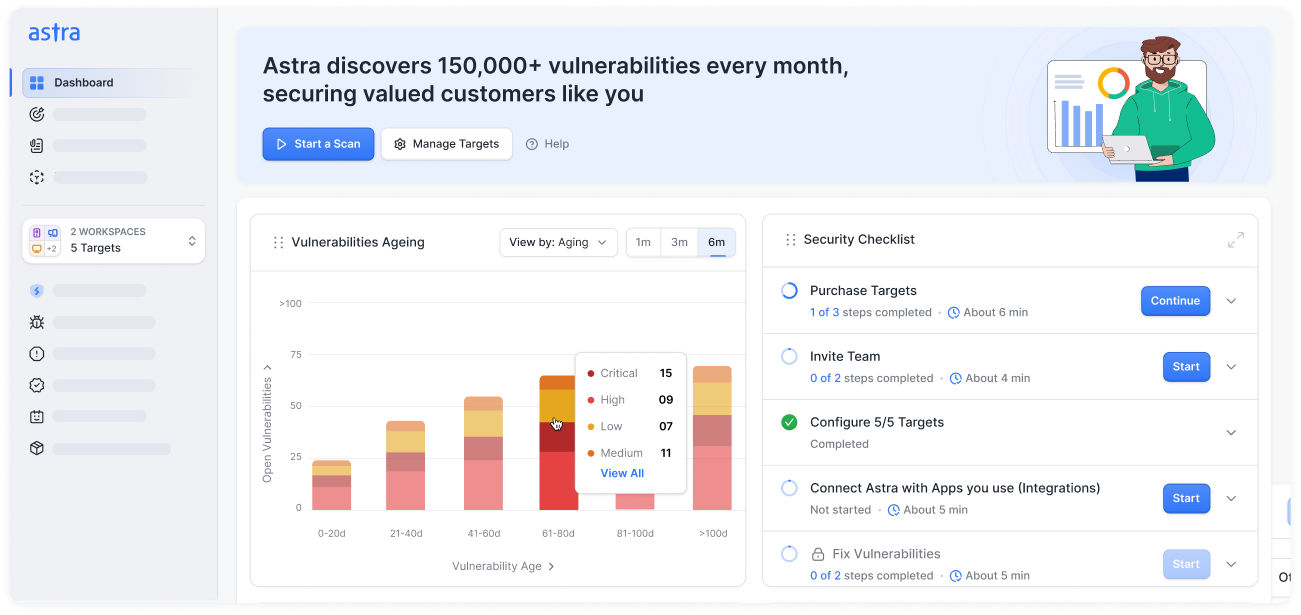










- Noise-filtered vulnerabilities with intelligent detection logic
- False positives? Get them vetted by our experts
- Mark false positives to skip them in future scans
- Additional white-glove vulnerability vetting by expert security engineers
- Audit-ready reports aligned with ISO, PCI, SOC 2, HIPAA, GDPR, OWASP, NIST, and more.
- Expert support to simplify assessments and pass audits faster.
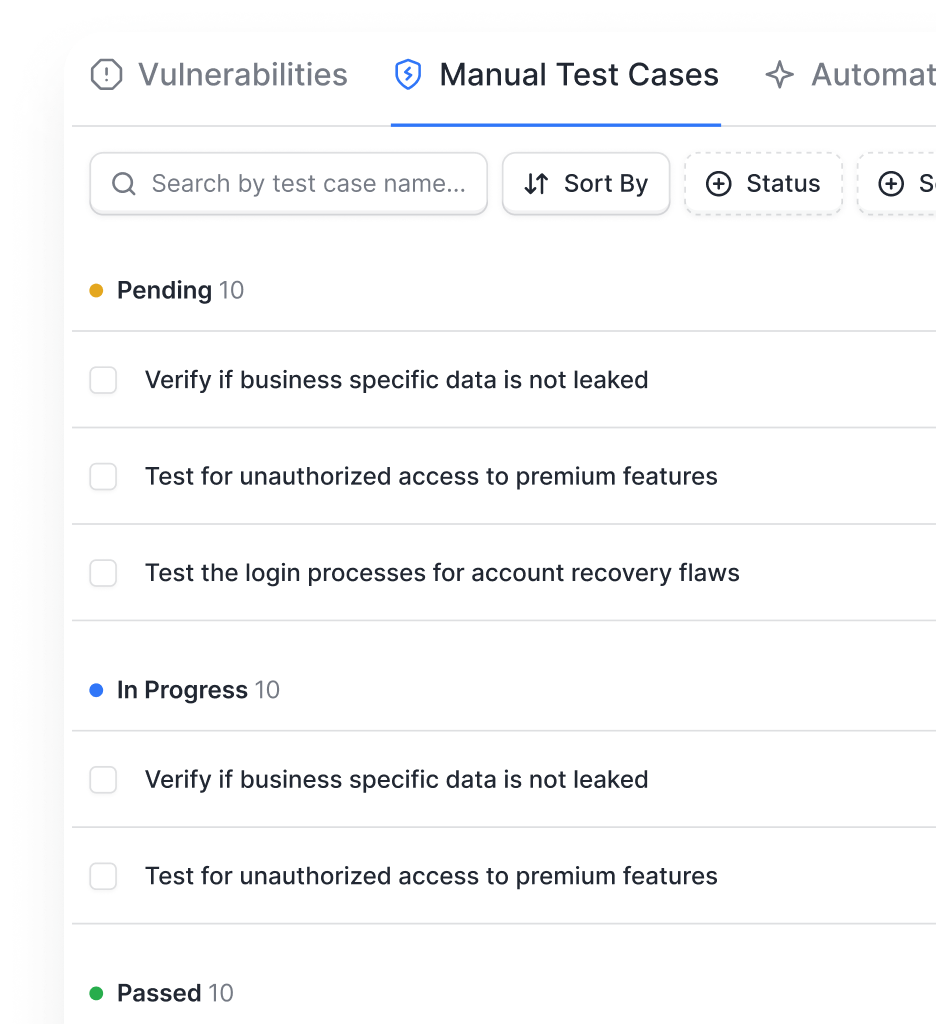
- Integrate into CI/CD with GitHub Actions, GitLab CI, Jenkins, Bitbucket, and more.
- Automate scans, send vulnerability alerts via Slack
- Create JIRA tickets, all without leaving your pipeline.
- Continuous, scheduled DAST scans for web apps, API, and cloud without manual setup or tuning.
- Expert-tuned accuracy with optimized scanners to reduce false positives.
- Vulnerabilities triaged and mapped to real business impact.
- Auto-generated compliance-grade summaries with remediation guidance and automated rescans for verification
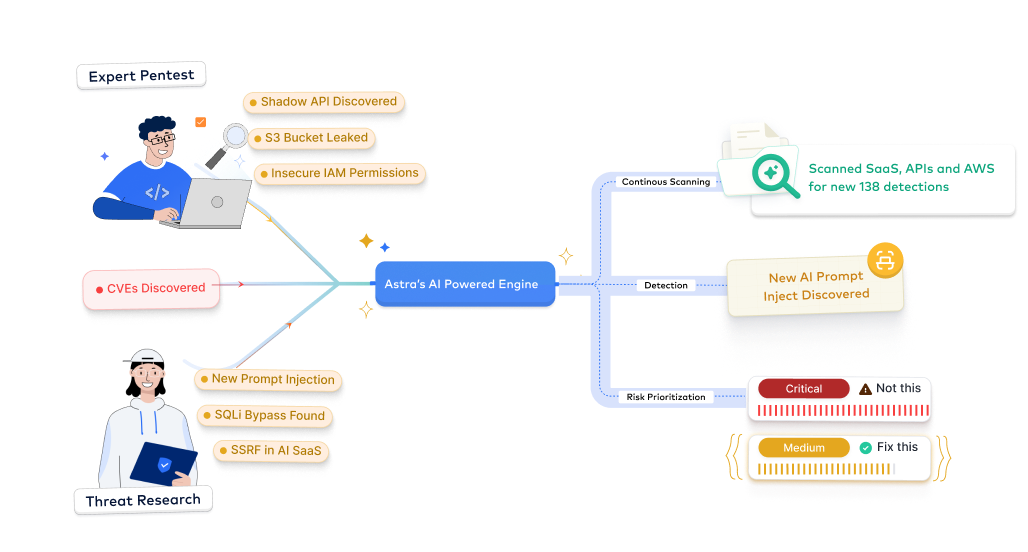
- Our AI tailors test scenarios to your unique app
- Contextual remediation advice at your fingertips
- Continuously improves detection accuracy through context-aware analysis and evolving ML models trained on real-world vulnerability patterns.

Astra's 7-Step Pentest Process
How our red team services work
From reconnaissance to post-exploitation analysis, Astra’s red team methodology uncovers weaknesses that mimic real-world threats. Our 6-step process replicates advanced adversary behavior with precision.
Reconnaissance and scoping


Threat modeling & attack planning
Lateral movement and persistence


Reporting and executive briefing
Remediation & verification


From startups to fortune companies,
1000+ companies trust Astra












































.webp)





Types of attacks we simulate
Our red team service provides comprehensive adversary simulation, testing your defenses against sophisticated real-world attack scenarios

Advanced Web Application Exploits

API & Microservices Attacks

Cloud & Infrastructure Compromise

Network & External Threat Simulation

Red-Team Logic & Workflow Attacks
Persistent & Stealth Threats





Experience the Astra Security difference: faster, smarter, compliance-ready pentesting.
Pentesting as a service, tailored for your industry
Continuous penetration testing and compliance mapping services built for ISO, SOC 2, HIPAA, PCI DSS, and more.

- Secure financial systems and payment workflows from logic flaws
- Deliver actionable fixes and maintain PCI DSS, ISO 27001, SOC 2, DORA compliance, and more
- Standards: OWASP, PTES, CVSS

- Protect patient data and secure APIs across web, mobile, and cloud
- Uncover hidden PHI exposures and validate HIPAA, ABHA, and more
- Standards: OWASP, PTES, NIST, CVSS

- Accelerate app security with DevSecOps integration and continuous scans
- Detect vulnerabilities with AI-driven validation and ensure ISO 27001, SOC 2, GDPR compliance and more
- Standards: OWASP, PTES, CVSS, NIST SP 800-115

- Protect customer data and secure payment flows from BOLA/IDOR risks
- Empower developers with guided remediation and PCI DSS, ISO 27001, SOC 2 compliance and more
- Standards: OWASP, PTES, CVSS

- Fortify cloud, container, and on-prem systems with authenticated tests
- Monitor and validate vulnerabilities to prevent downtime; comply with NIST, ISO 27001, SOC 2, CREST, Cert-In, and more
- Standards: OWASP, PTES, NIST, CVSS

- Discover shadow APIs and secure cloud services
- Deliver fast, developer-friendly fixes; ensure GDPR, ISO 27001, SOC 2 compliance
- Standards: OWASP, PTES, CVSS
Our pentesters? World class, certified & contributors to top security projects
We find the bugs before the bad guys do
Our team stays ahead of the curve in the ever-evolving world of web security

.avif)
.avif)
.avif)





Stay compliant throughout the year
Understand our industry-specific pentests as a service plans designed to meet your compliance, scale, and security needs.
- Get compliance-ready year-round for ISO 27001, SOC 2, GDPR, HIPAA, PCI DSS, CREST, CERT-In, CIS Controls, NIST, & more
- Receive actionable insights from continuous pentesting and expert-led remediation guidance
- Track compliance progress with the Astra Security Compliance View, providing executive-friendly and technical views


- Maintain audit-ready reports without manual effort
- Reduce risk exposure with real-time detection and validation
- Prioritize remediation based on business impact and compliance requirements
- Demonstrate security maturity to clients, regulators, and internal stakeholders


Frequently asked questions
What are red team services, and how do they differ from a penetration test?
Red team services simulate real-world attacks to test an organization’s overall defenses and response, while a penetration test focuses on identifying technical vulnerabilities within a defined scope and providing remediation steps.
How long does a Red team exercise typically take, and how often should it be conducted?
A Red team exercise usually lasts several weeks to months, depending on scope and complexity. For optimal resilience, organizations should conduct Red team exercises at least annually or as threat landscapes evolve.
How are findings reported, and how does remediation work after a Red team exercise?
Findings are compiled in detailed reports with exploit paths, risk ratings, and executive summaries. Remediation involves prioritizing fixes, implementing security controls, and retesting to validate vulnerability mitigation.
What are the limitations of red team services, and why are follow-up measures important?
Red teaming may miss full coverage of all systems and might not satisfy compliance, since it targets stealthy, high-value goals. Follow-up measures like penetration testing and remediation are important to address gaps and ensure comprehensive security.











