#1 Vulnerability Scanning Services (Trusted by 1000+ Teams)
Detect and validate vulnerabilities across web, API, and cloud layers with continuous automated vulnerability scanning services. Our team pairs tuned automation with expert review to remove false positives, map findings to compliance, and hand engineers prioritized, SLA-backed remediation steps.

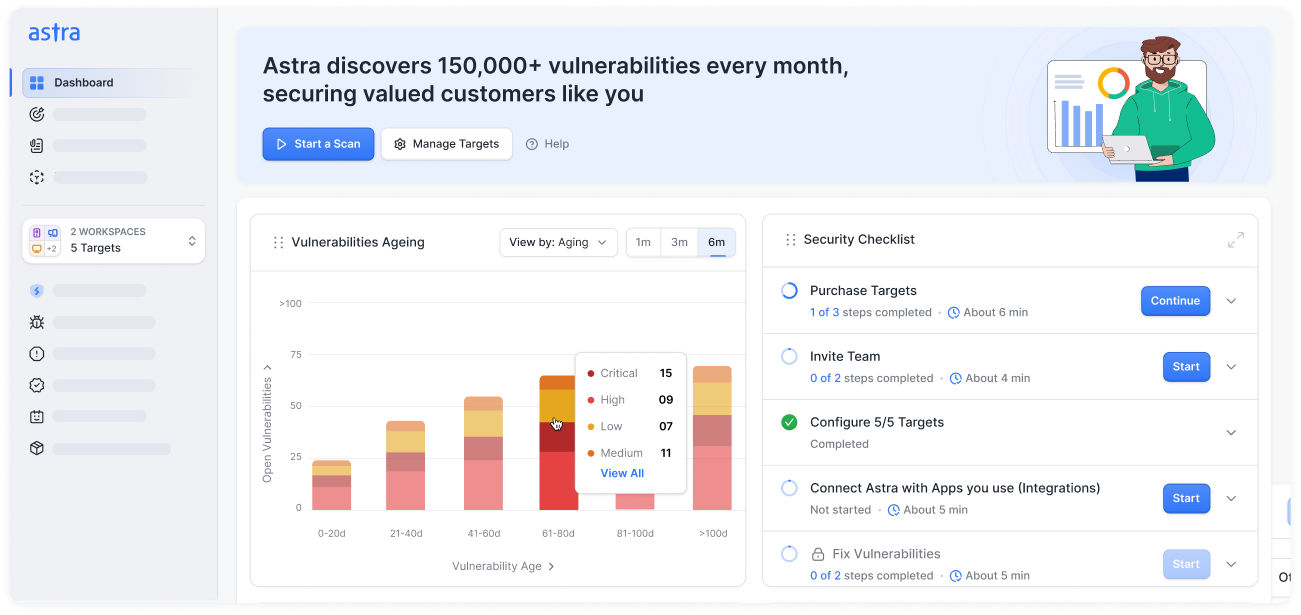










Why choose Astra Security's vulnerability scanning services?
Experience our DAST, API, and cloud scanner plans built for modern security teams with expert-driven testing, smart automation, and continuous protection at scale.
- Focus on real vulnerabilities with noise-free detection logic
- Our experts vet false positives so you don’t waste hours validating noise
- Mark verified issues once to skip them in future scans
- Get expert vulnerability reviews for faster prioritization
- Cut manual tuning as our AI-first vulnerability scanner adapts tests to your app
- Context-aware analysis improves accuracy & guidance with every scan
- Use machine learning models that evolve from real-world exploit data
- Scale testing without increasing security headcount
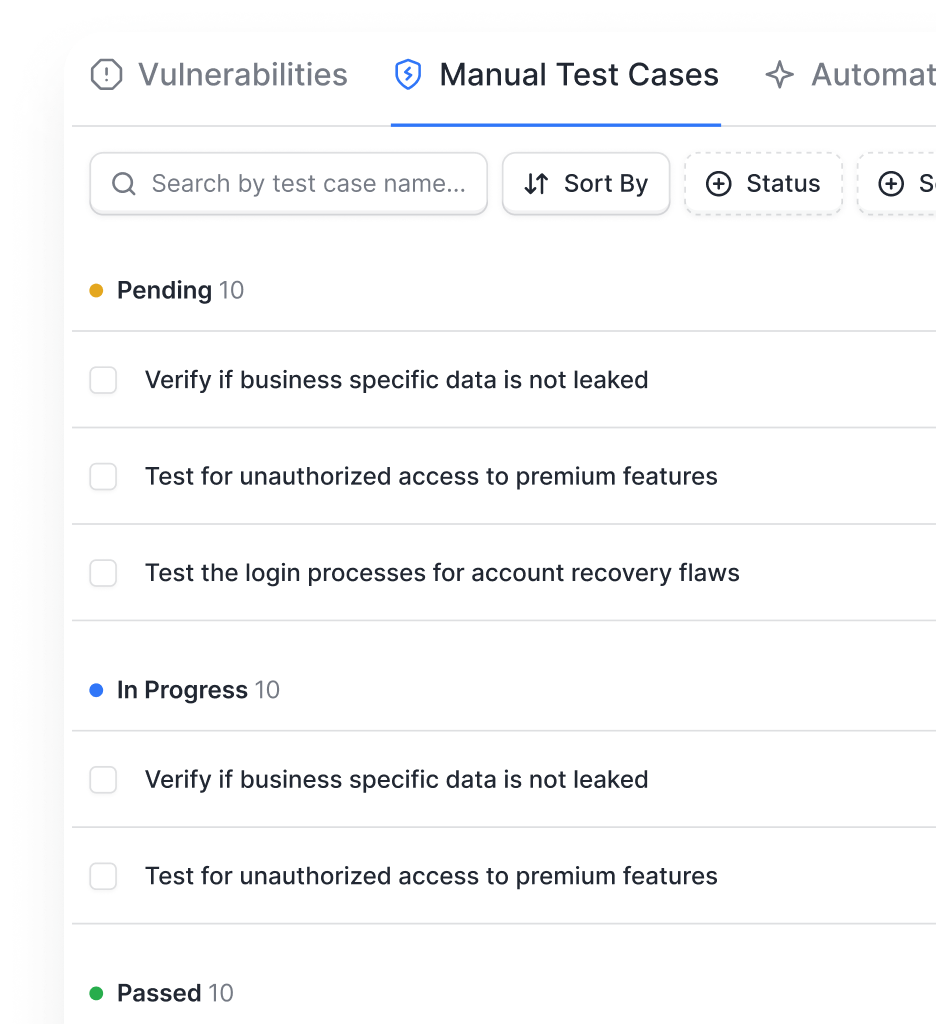
- Get continuous protection across web, API, and cloud
- Avoid alert fatigue with business-impact optimized vulnerabilities & expert-tuned DAST scans
- Stay compliant with automated reports, verified fixes, and targeted automated rescans
- Cut false positives and reduce total cost with managed accuracy of vetted scans
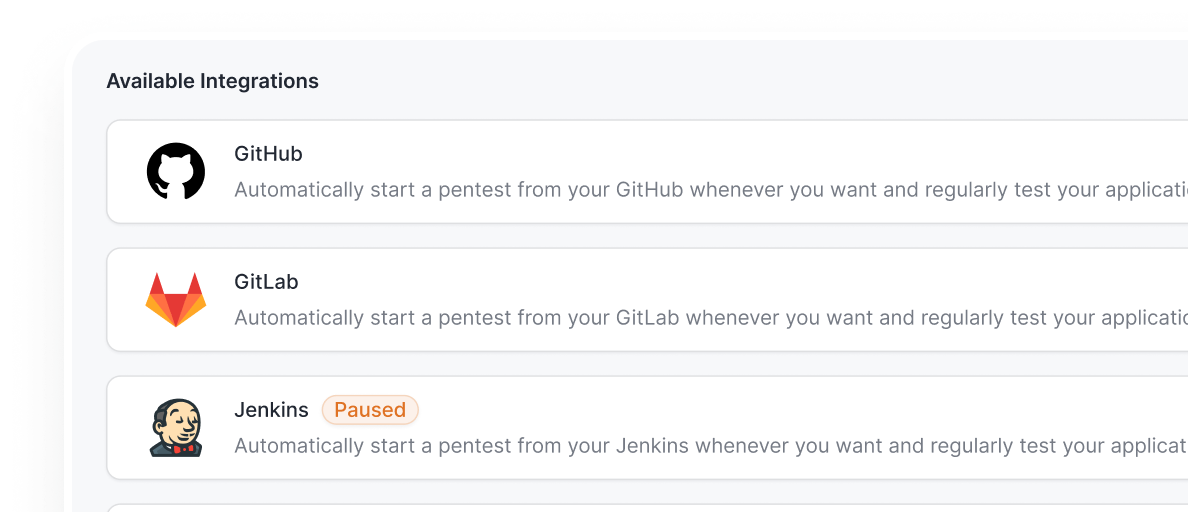
- Integrate testing seamlessly into your CI/CD workflows (GitHub, GitLab, CI, Jenkins, Bitbucket, & more) with zero release delays
- Automate scans, Slack vulnerability alerts, and JIRA ticketing to cut manual work
- Shorten your mean time to remediate with seamless vulnerability workflows
- Maintain speed-to-market without compromising security
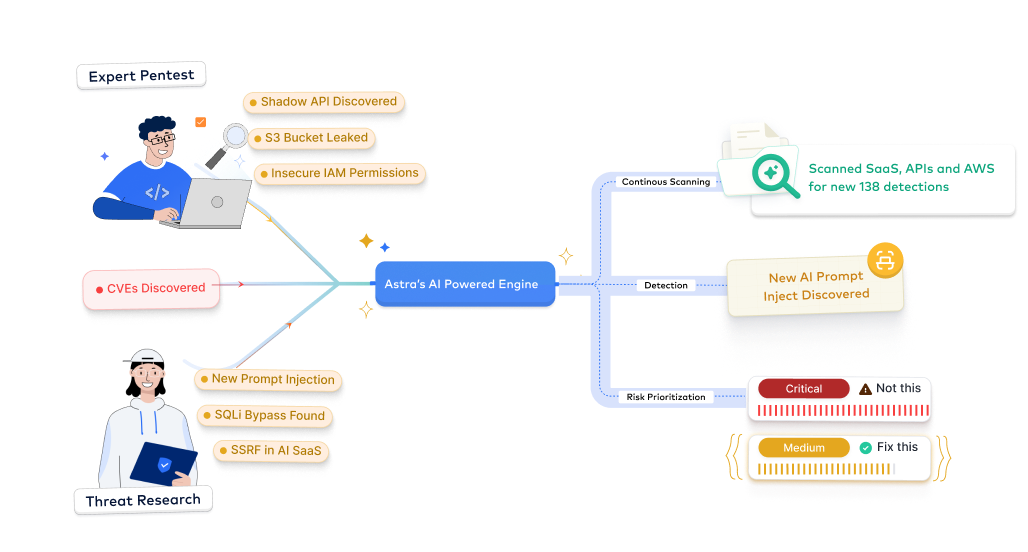
- Generate detailed scan reports with vulnerabilities mapped to ISO, PCI, SOC 2, HIPAA, GDPR, OWASP, NIST, and other standards
- Demonstrate security maturity to shorten sales cycles
- Turn compliance readiness into a sales advantage

Astra's 7-Step Pentest Process
How our vulnerability scanning works
Astra’s 7-step pentest process combines intelligent automation with human expertise to deliver high-fidelity results trusted by CXOs. Every scan is fine-tuned to business risk, not noise.
Discovery & Scoping


Authentication Setup
Risk Scoring


Remediation Support
Re-Scan & Validate


From startups to fortune companies,
1000+ companies trust Astra












































.webp)





Types of vulnerabilities we detect
Our vulnerability scanning services provide full coverage, targeting vulnerabilities wherever they emerge

Web Application Vulnerabilities

API Security Flaws

Cloud & Configuration Exposures

Network & External Attack Surface

Business Logic & Authorization Issues
Compliance-Related Risks





Experience the Astra Security difference: faster, smarter, compliance-ready pentesting.
Pentesting as a service, tailored for your industry
Continuous penetration testing and compliance mapping services built for ISO, SOC 2, HIPAA, PCI DSS, and more.

- Secure financial systems and payment workflows from logic flaws
- Deliver actionable fixes and maintain PCI DSS, ISO 27001, SOC 2, DORA compliance, and more
- Standards: OWASP, PTES, CVSS

- Protect patient data and secure APIs across web, mobile, and cloud
- Uncover hidden PHI exposures and validate HIPAA, ABHA, and more
- Standards: OWASP, PTES, NIST, CVSS

- Accelerate app security with DevSecOps integration and continuous scans
- Detect vulnerabilities with AI-driven validation and ensure ISO 27001, SOC 2, GDPR compliance and more
- Standards: OWASP, PTES, CVSS, NIST SP 800-115

- Protect customer data and secure payment flows from BOLA/IDOR risks
- Empower developers with guided remediation and PCI DSS, ISO 27001, SOC 2 compliance and more
- Standards: OWASP, PTES, CVSS

- Fortify cloud, container, and on-prem systems with authenticated tests
- Monitor and validate vulnerabilities to prevent downtime; comply with NIST, ISO 27001, SOC 2, CREST, Cert-In, and more
- Standards: OWASP, PTES, NIST, CVSS

- Discover shadow APIs and secure cloud services
- Deliver fast, developer-friendly fixes; ensure GDPR, ISO 27001, SOC 2 compliance
- Standards: OWASP, PTES, CVSS
Our pentesters? World class, certified & contributors to top security projects
We find the bugs before the bad guys do
Our team stays ahead of the curve in the ever-evolving world of web security

.avif)
.avif)
.avif)





Stay compliant throughout the year
Understand our industry-specific pentests as a service plans designed to meet your compliance, scale, and security needs.
- Get compliance-ready year-round for ISO 27001, SOC 2, GDPR, HIPAA, PCI DSS, CREST, CERT-In, CIS Controls, NIST, & more
- Receive actionable insights from continuous pentesting and expert-led remediation guidance
- Track compliance progress with the Astra Security Compliance View, providing executive-friendly and technical views


- Maintain audit-ready reports without manual effort
- Reduce risk exposure with real-time detection and validation
- Prioritize remediation based on business impact and compliance requirements
- Demonstrate security maturity to clients, regulators, and internal stakeholders


Frequently asked questions
What is vulnerability scanning, and how does it work?
Vulnerability scanning is an automated process that identifies security weaknesses across your systems by probing networks, apps, and cloud assets. It continuously detects vulnerabilities, allowing you to prioritize and remediate risks before attackers can exploit them.
Why is vulnerability scanning important for businesses?
Vulnerability scanning services enable businesses to proactively identify security gaps, mitigate breach risks, and ensure regulatory compliance. Regular scanning ensures that new threats and misconfigurations are quickly caught and addressed to protect sensitive data.
What is the difference between vulnerability scanning and penetration testing?
Vulnerability scanning is an automated process that continuously detects known weaknesses, whereas penetration testing is a manual, in-depth attempt to exploit vulnerabilities. Both complement each other: scanning provides ongoing coverage, and penetration testing validates critical risks.
Can vulnerability scanning help with compliance?
Yes, vulnerability scanning services support compliance by identifying and reporting security gaps relevant to standards like PCI, HIPAA, ISO 27001, and GDPR, helping organizations meet audit requirements efficiently.
Do I need both automated and manual vulnerability scanning?
Combining automated scans with manual vulnerability testing provides the best security posture by ensuring the rapid detection and thorough verification of complex vulnerabilities that machines alone may miss.
What happens after a vulnerability scan is completed?
After scanning, detailed reports categorize vulnerabilities by risk level and provide remediation guidance. Teams prioritize fixes, apply patches, and schedule rescans to verify success and maintain continuous protection.











